
Welcome! We go directly to the topic. This is a blog about Microsoft SC-200 exam questions.
We shared the newly updated Microsoft SC-200 exam questions and answers. You can practice the test online.
You can also download the SC-200 exam PDF online for free on Google Drive.
All free content comes from leads4pass sc-200 exam dumps https://www.leads4pass.com/sc-200.html (PDF+VCE).
leads4pass has complete SC-200 exam questions and answers. All exam questions have been updated to ensure immediate validity!
Microsoft SC-200 exam discount code comes from leads4pass
Our topic today includes the exam discount code for sc-200, so here’s a look at the latest updates for 2021!
Microsoft sc-200 Exam pdf
Microsoft sc-200 Exam pdf is part of the leads4pass sc-200 exam dumps, and free content is also up-to-date,
helping you stay up-to-date with some of the latest exam content
Microsoft sc-200 free online practice test
QUESTION #1
You have a Microsoft 365 subscription that uses Microsoft Defender for Office 365.
You have Microsoft SharePoint Online sites that contain sensitive documents.
The documents contain customer account numbers that each consists of 32 alphanumeric characters.
You need to create a data loss prevention (DLP) policy to protect sensitive documents.
What should you use to detect which documents are sensitive?
A. SharePoint search
B. a hunting query in Microsoft 365 Defender
C. Azure Information Protection
D. RegEx pattern matching
Correct Answer: C
Reference: https://docs.microsoft.com/en-us/azure/information-protection/what-is-information-protection
QUESTION #2
DRAG-DROP
You open the Cloud App Security portal as shown in the following exhibit.
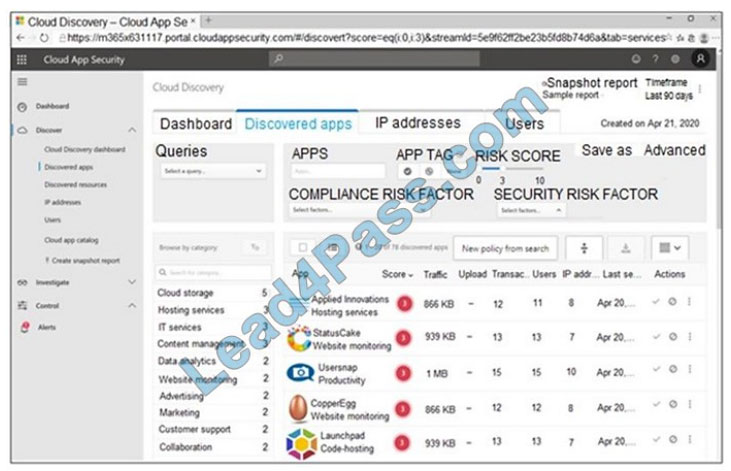
You need to remediate the risk for the Launchpad app.
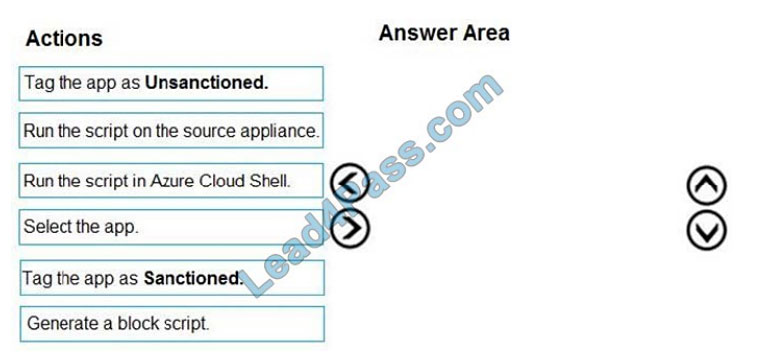
Which four actions should you perform in sequence?
To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
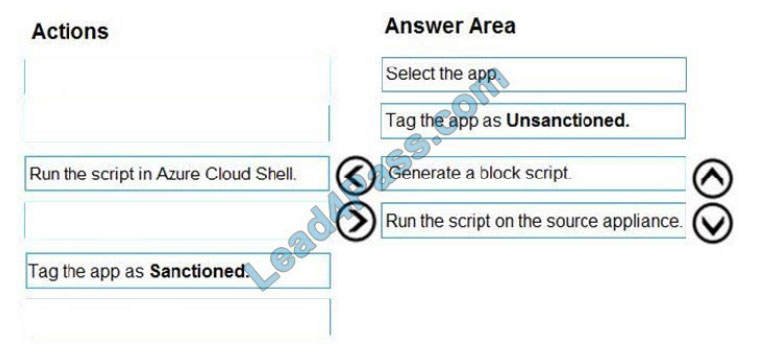
Correct Answer:
QUESTION #3
Note: This question is part of a series of questions that present the same scenario.
Each question in the series contains a unique solution that might meet the stated goals.
Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it.
As a result, these questions will not appear on the review screen.
You are configuring Microsoft Defender for Identity integration with Active Directory.
From the Microsoft Defender for identity portal, you need to configure several accounts for attackers to exploit.
Solution: From Entity tags, you add the accounts as Honeytoken accounts.
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
Reference: https://docs.microsoft.com/en-us/defender-for-identity/manage-sensitive-honeytoken-accounts
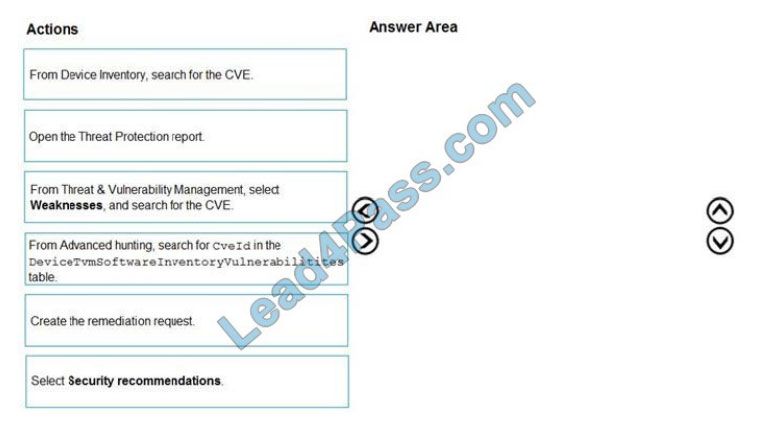
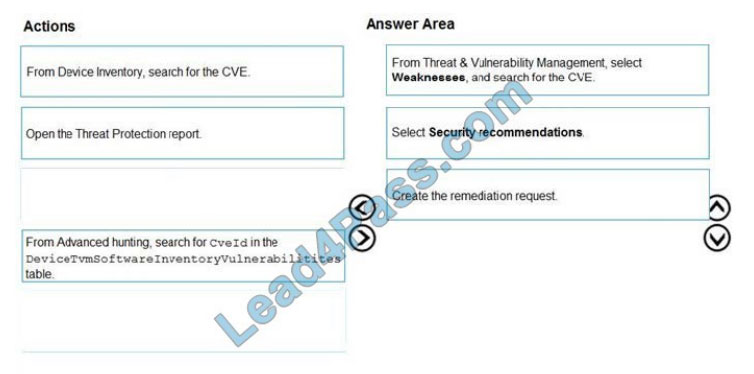
QUESTION #4
DRAG-DROP
You are informed of a new common vulnerabilities and exposures (CVE) vulnerability that affects your environment.
You need to use Microsoft Defender Security Center to request remediation from the team responsible for the affected
systems if there is a documented active exploit available.
Which three actions should you perform in sequence?
To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
Correct Answer:
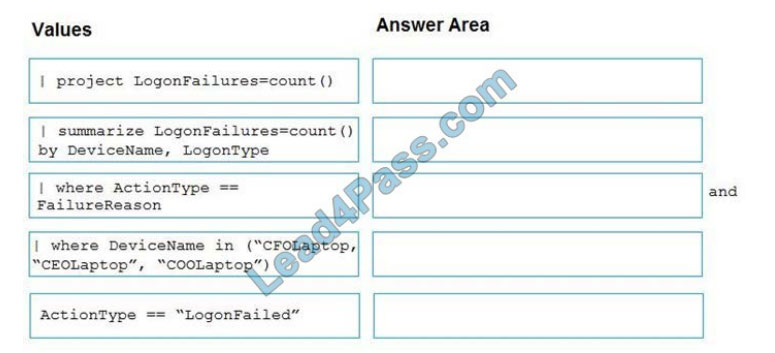
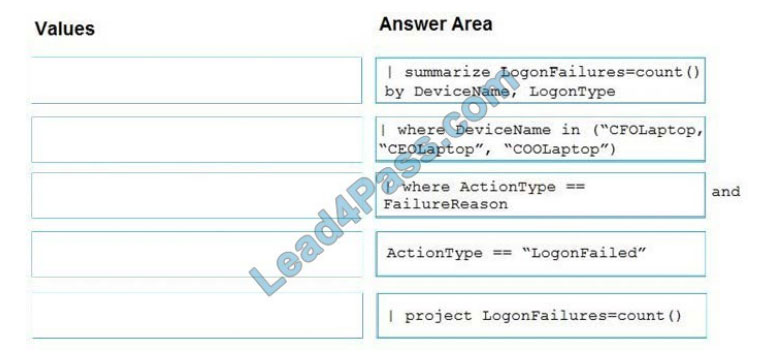
QUESTION #5
DRAG-DROP
You are investigating an incident by using Microsoft 365 Defender.
You need to create an advanced hunting query to detect failed sign-in authentications on three devices named CFOLaptop, CEOLaptop, and COOLaptop.
How should you complete the query?
To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Select and Place:
QUESTION #6
Your company uses Azure Sentinel to manage alerts from more than 10,000 IoT devices.
A security manager at the company reports that tracking security threats is increasingly difficult due to a large number
of incidents.
You need to recommend a solution to provide a custom visualization to simplify the investigation of threats and to infer threats by using machine learning.
What should you include in the recommendation?
A. built-in queries
B. Livestream
C. notebooks
D. bookmarks
Correct Answer: C
Reference: https://docs.microsoft.com/en-us/azure/sentinel/notebooks
QUESTION #7
Note:
This question is part of a series of questions that present the same scenario.
Each question in the series contains a unique solution that might meet the stated goals.
Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it.
As a result, these questions will not appear on the review screen.
You use Azure Security Center. You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
Solution: From Security alerts, you select the alert, select Take Action, and then expand the Mitigate the threat section.
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
QUESTION #8
Your company uses Azure Security Center and Azure Defender.
The security operations team at the company informs you that it does NOT receive email notifications for security
alerts.
What should you configure in Security Center to enable the email notifications?
A. Security solutions
B. Security policy
C. Pricing and settings
D. Security alerts
E. Azure Defender
Correct Answer: C
QUESTION #9
HOTSPOT
You manage the security posture of an Azure subscription that contains two virtual machines named vm1 and vm2.
The secure score in Azure Security Center is shown in the Security Center exhibit. (Click the Security Center tab.)
Azure Policy assignments are configured as shown in the Policies exhibit. (Click the Policies tab.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:

QUESTION #10
You need to visualize Azure Sentinel data and enrich the data by using third-party data sources to identify indicators of
compromise (IoC).
What should you use?
A. notebooks in Azure Sentinel
B. Microsoft Cloud App Security
C. Azure Monitor
D. hunting queries in Azure Sentinel
Correct Answer: A
Reference: https://docs.microsoft.com/en-us/azure/sentinel/notebooks
QUESTION #11
DRAG-DROP
You plan to connect an external solution that will send Common Event Format (CEF) messages to Azure Sentinel.
You need to deploy the log forwarder.
Which three actions should you perform in sequence?
To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
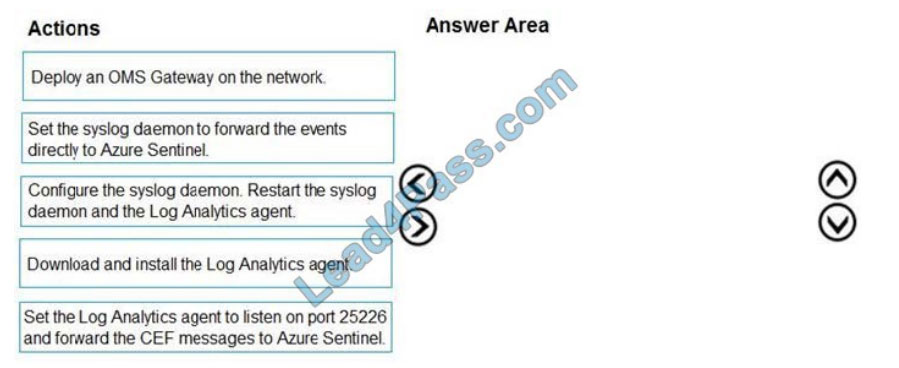
Correct Answer:
QUESTION #12
DRAG-DROP
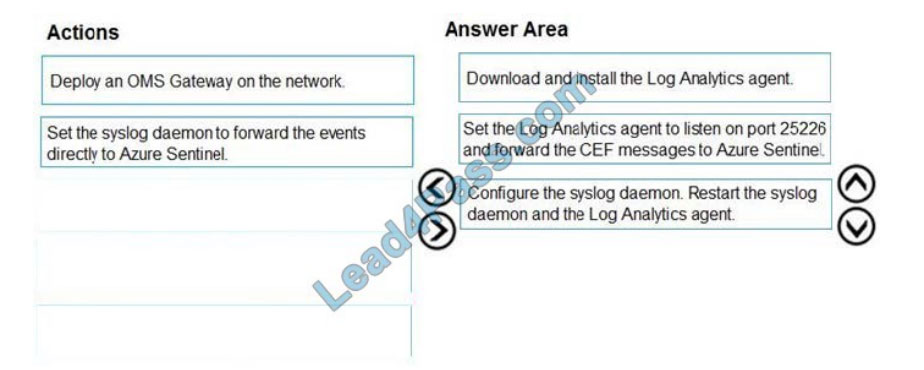
You create a new Azure subscription and start collecting logs for Azure Monitor.
You need to configure Azure Security Center to detect possible threats related to sign-ins from suspicious IP addresses
to Azure virtual machines.
The solution must validate the configuration.
Which three actions should you perform in a sequence?
To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:

Correct Answer:
QUESTION #13
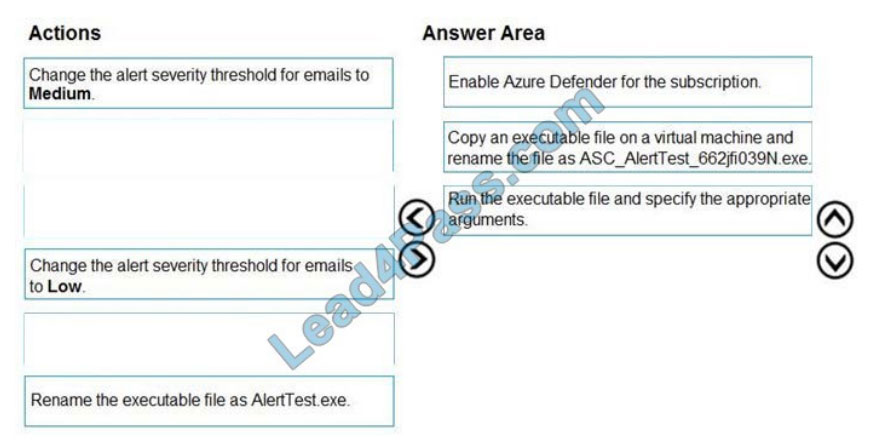
You provision a Linux virtual machine in a new Azure subscription.
You enable Azure Defender and onboard the virtual machine to Azure Defender.
You need to verify that an attack on the virtual machine triggers an alert in Azure Defender.
Which two Bash commands should you run on the virtual machine?
Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. cp /bin/echo ./asc_alerttest_662jfi039n
B. ./alerttest testing eicar pipe
C. cp /bin/echo ./alerttest
D. ./asc_alerttest_662jfi039n testing eicar pipe
Correct Answer: AD
QUESTION #14
You provision Azure Sentinel for a new Azure subscription.
You are configuring the Security Events connector.
While creating a new rule from a template in the connector, you decide to generate a new alert for every event.
You create the following rule query.
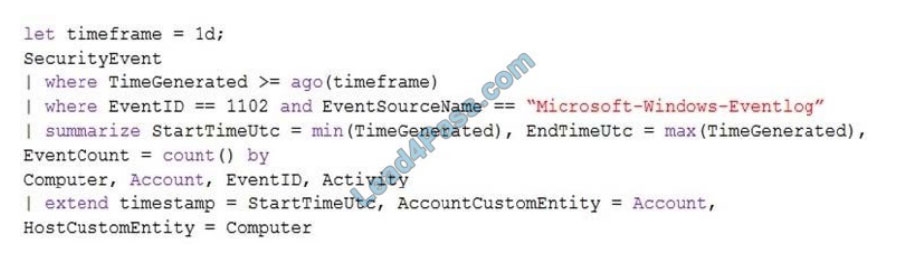
By which two components can you group alerts into incidents?
Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. user
B. resource group
C. IP address
D. computer
Correct Answer: CD
QUESTION #15
You have a playbook in Azure Sentinel. When you trigger the playbook, it sends an email to a distribution group.
You need to modify the playbook to send the email to the owner of the resource instead of the distribution group.
What should you do?
A. Add a parameter and modify the trigger.
B. Add a custom data connector and modify the trigger.
C. Add a condition and modify the action.
D. Add a parameter and modify the action.
Correct Answer: D
Reference: https://azsec.azurewebsites.net/2020/01/19/notify-azure-sentinel-alert-to-your-email-automatically/
Summary:
This article shares the latest updated Microsoft sc-200 exam dump https://www.leads4pass.com/sc-200.html (Total Questions: 84 Q&A). Free online practice test, free online download of exam pdf, and leads4pass 15% exam discount code 2021.
ps.
Microsoft sc-200 Exam pdf is part of the leads4pass sc-200 exam dumps, and free content is also up-to-date,
helping you stay up-to-date with some of the latest exam content

