
The latest update and the actual 100% pass to ensure that the Microsoft Certified SC-900 dumps from leads4pass: https://www.leads4pass.com/sc-900.html (98 Q&A),
leads4pass provides SC-900 VCE dumps and SC-900 PDF dumps to prepare for the Microsoft Certified: Security, Compliance, and Identity Fundamentals exam. 100% effective and 100% pass guaranteed.
In addition to participating in the online test! You can download a free SC-900 dumps PDF online: https://drive.google.com/file/d/1NcJn8vhJFYXliqostMLXU3vBUp4mIPd0/
Free Microsoft Certified SC-900 exam questions and answers
The answer is announced at the end of the article
QUESTION 1
Which Azure Active Directory (Azure AD) feature can you use to provide just-in-time (JIT) access to manage Azure
resources?
A. conditional access policies
B. Azure AD Identity Protection
C. Azure AD Privileged Identity Management (PIM)
D. authentication method policies
Azure AD Privileged Identity Management (PIM) provides just-in-time privileged access to Azure AD and Azure
resources
Reference: https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
QUESTION 2
HOTSPOT
You have a Microsoft 365 E5 tenant.
You create sensitivity labels as shown in the Sensitivity Labels exhibit.
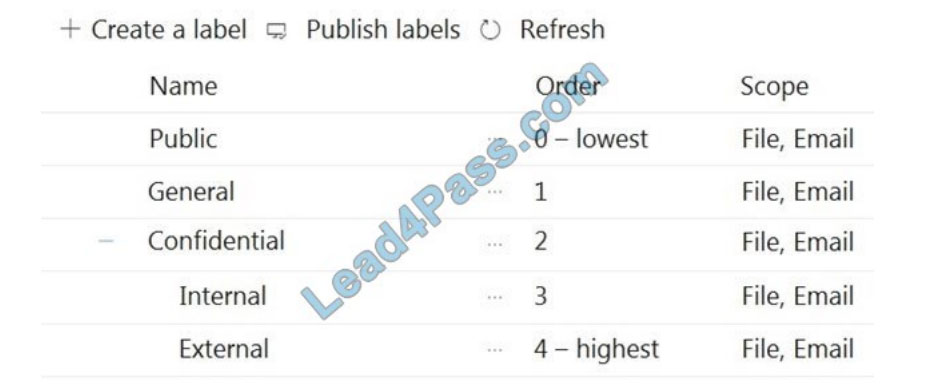
The Confidential/External sensitivity label is configured to encrypt files and emails when applied to content. The
sensitivity labels are published as shown in the Published exhibit.

For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct
selection is worth one point.
Hot Area:

Correct Answer:

Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide
QUESTION 3
Which score measures an organization\\’s progress in completing actions that help reduce risks associated to data
protection and regulatory standards?
A. Microsoft Secure Score
B. Productivity Score
C. Secure score in Azure Security Center
D. Compliance score
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-manager?view=o365-worldwide
https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-score-calculation?view=o365-worldwide
QUESTION 4
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:

Reference: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
QUESTION 5
HOTSPOT
Select the answer that correctly completes the sentence.
Hot Area:
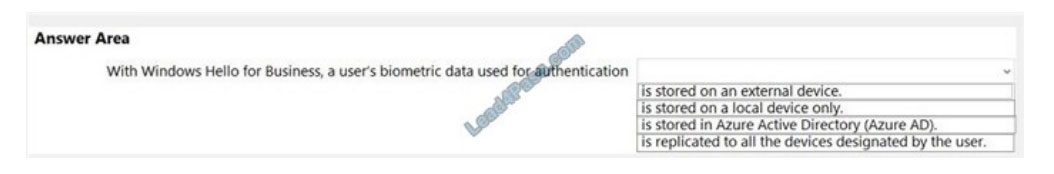
Correct Answer:

Biometrics templates are stored locally on a device.
Reference: https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-overview
QUESTION 6
HOTSPOT
Select the answer that correctly completes the sentence.
Hot Area:

Correct Answer:

Microsoft Azure Sentinel is a scalable, cloud-native, security information event management (SIEM) and security
orchestration automated response (SOAR) solution.
Reference: https://docs.microsoft.com/en-us/azure/sentinel/overview
QUESTION 7
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
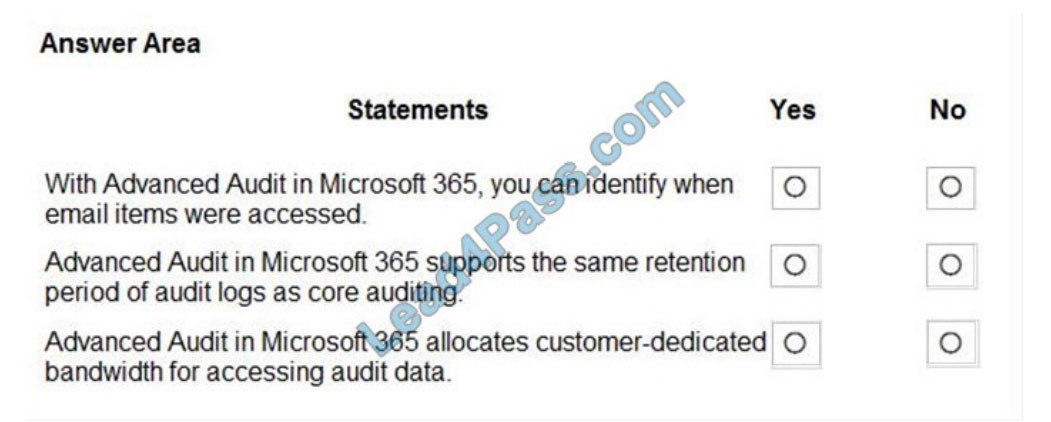
Correct Answer:
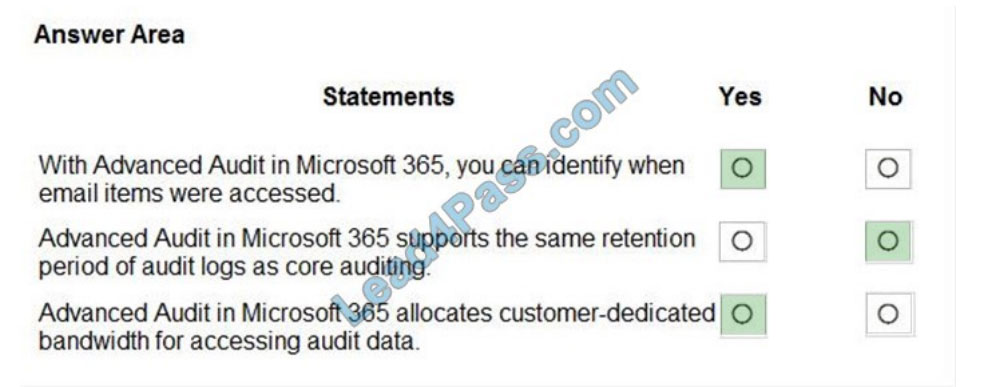
Box 1: Yes
The MailItemsAccessed event is a mailbox auditing action and is triggered when mail data is accessed by mail protocols
and mail clients.
Box 2: No
Basic Audit retains audit records for 90 days.
Advanced Audit retains all Exchange, SharePoint, and Azure Active Directory audit records for one year. This is
accomplished by a default audit log retention policy that retains any audit record that contains the value of Exchange,
SharePoint,
or AzureActiveDirectory for the Workload property (which indicates the service in which the activity occurred) for one
year.
Box 3: yes
Advanced Audit in Microsoft 365 provides high-bandwidth access to the Office 365 Management Activity API.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/advanced-audit?view=o365-worldwide
https://docs.microsoft.com/en-us/microsoft-365/compliance/auditing-solutions-overview?view=o365-worldwide#licensingrequirements
https://docs.microsoft.com/en-us/office365/servicedescriptions/microsoft-365-service-descriptions/microsoft-365-tenantlevel-services-licensing-guidance/microsoft-365-security-compliance-licensing-guidance#advanced-audit
QUESTION 8
You plan to implement a security strategy and place multiple layers of defense throughout a network infrastructure.
Which security methodology does this represent?
A. threat modeling
B. identity as the security perimeter
C. defense in depth
D. the shared responsibility model
QUESTION 9
Which Azure Active Directory (Azure AD) feature can you use to restrict Microsoft Intune-managed devices from
accessing corporate resources?
A. network security groups (NSGs)
B. Azure AD Privileged Identity Management (PIM)
C. conditional access policies
D. resource locks
QUESTION 10
HOTSPOT
Select the answer that correctly completes the sentence.
Hot Area:
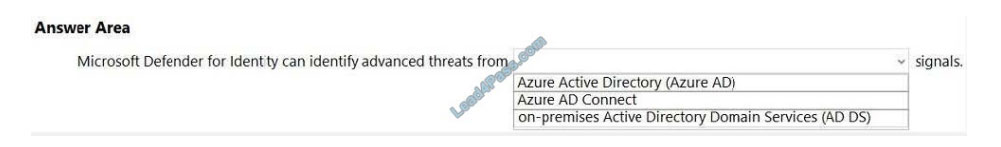
Correct Answer:
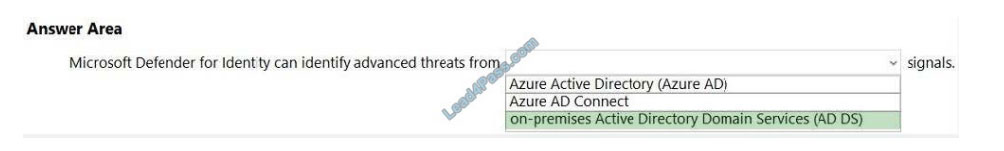
Microsoft Defender for Identity is a cloud-based security solution that leverages your on-premises Active Directory
signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions
directed at your organization.
Reference: https://docs.microsoft.com/en-us/defender-for-identity/what-is
QUESTION 11
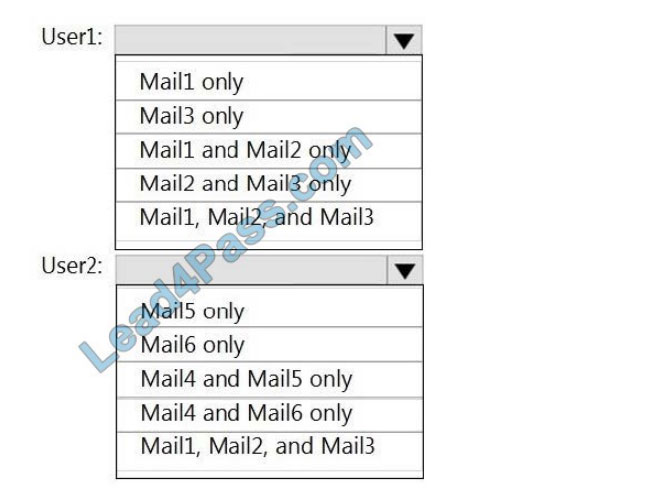
HOTSPOT
You have a Microsoft 365 tenant named contoso.com that contains two users named User1 and User2. The tenant uses
Microsoft Office 365 Message Encryption
(OME).
User1 plans to send emails that contain attachments as shown in the following table.
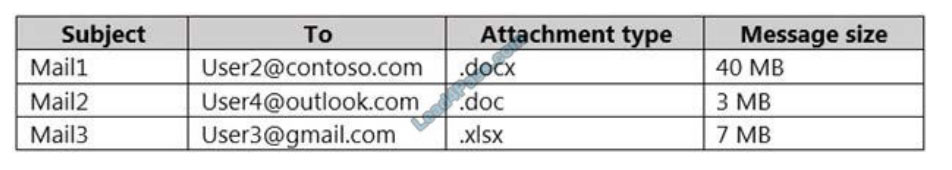
User2 plans to send emails that contain attachments as shown in the following table.
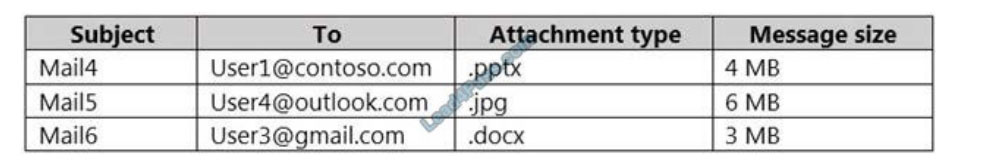
For which emails will the attachments be protected? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
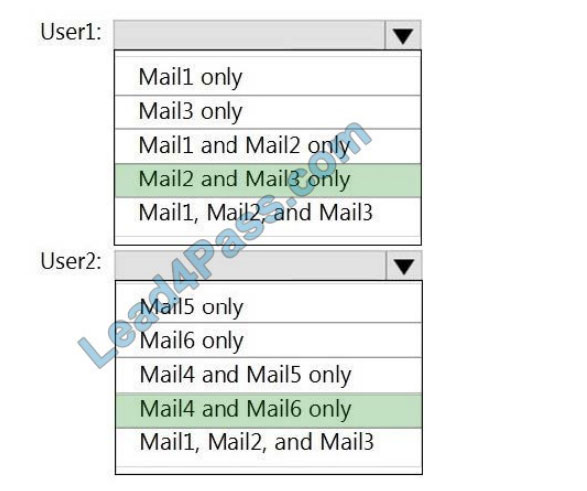
Reference: https://support.microsoft.com/en-gb/office/introduction-to-irm-for-email-messagesbb643d33-4a3f-4ac7-9770-fd50d95f58dc?ui=en-usandrs=en-gbandad=gb#FileTypesforIRM
https://docs.microsoft.com/en-us/microsoft-365/compliance/ome?view=o365-worldwide https://docs.microsoft.com/enus/office365/servicedescriptions/exchange-online-service-description/exchange-online-limits#message-limits-1
QUESTION 12
You have a new Microsoft 365 tenant.
You need to ensure that custom trainable classifiers can be created in the tenant.
To which role should you be assigned to perform the configuration?
A. Security administrator
B. Security operator
C. Global administrator
D. Compliance administrator
QUESTION 13
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:

Reference: https://docs.microsoft.com/en-us/azure/governance/policy/overview
Verify answer
| Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 |
| C | IMAGE | D | IMAGE | IMAGE | IMAGE | IMAGE | C | C | IMAGE | IMAGE | D | IMAGE |
Continue to follow to get more free updates…
By using the leads4pass SC-900 dumps with PDF and VCE, 100% of the first pass the exam is guaranteed: https://www.leads4pass.com/sc-900.html (98 Q&As, VCE and PDF)
ps. leads4pass shares a part of SC-900 dumps PDF for free: https://drive.google.com/file/d/1NcJn8vhJFYXliqostMLXU3vBUp4mIPd0/

