Latest leads4pass 210-260 dumps Cisco CCNA Security pdf practice questions and answers free update. The best and most Cisco CCNA Security 210-260 dumps vce youtube demo update free shared. “Implementing Cisco Network Security” is the name of Cisco CCNA Security https://www.leads4pass.com/210-260.html exam dumps which covers all the knowledge points of the real Cisco exam. High quality Cisco CCNA Security 210-260 dumps exam training materials and study guides free try, pass Cisco 210-260 exam test easily.
Latest Cisco 210-260 dumps pdf questions and answers free download: https://drive.google.com/open?id=0B_7qiYkH83VRcnI0SE83bHBvQ1k
Latest Cisco 200-310 dumps pdf questions and answers free download: https://drive.google.com/open?id=0B_7qiYkH83VROXBqSzZWaThrVlE
Vendor: Cisco
Certifications: CCNA Security
Exam Name: Implementing Cisco Network Security
Exam Code: 210-260
Total Questions: 310 Q&As
QUESTION 1
What is one requirement for locking a wired or wireless device from ISE?
A. The ISE agent must be installed on the device.
B. The device must be connected to the network when the lock command is executed.
C. The user must approve the locking action.
D. The organization must implement an acceptable use policy allowing device locking.
Correct Answer: A
QUESTION 2
Which syslog severity level is level number 7?
A. Warning
B. Informational
C. Notification
D. Debugging
Correct Answer: D
QUESTION 3
In which three ways does the RADIUS protocol differ from TACACS? (Choose three.)
A. RADIUS uses UDP to communicate with the NAS.
B. RADIUS encrypts only the password field in an authentication packet.
C. RADIUS authenticates and authorizes simultaneously, causing fewer packets to be transmitted.
D. RADIUS uses TCP to communicate with the NAS.
E. RADIUS can encrypt the entire packet that is sent to the NAS.
F. RADIUS supports per-command authorization.
Correct Answer: ABC
QUESTION 4
According to Cisco best practices, which three protocols should the default ACL allow on an access port to enable wired BYOD devices to supply valid credentials and connect to the network? (Choose three.)
A. BOOTP
B. TFTP
C. DNS
D. MAB
E. HTTP
F. 802.1x
Correct Answer: ABC
QUESTION 5
210-260 dumps In which stage of an attack does the attacker discover devices on a target network?
A. Reconnaissance
B. Covering tracks
C. Gaining access
D. Maintaining access
Correct Answer: A
QUESTION 6
Refer to the exhibit.
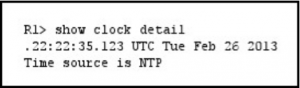
Which statement about the device time is true?
A. The time is authoritative, but the NTP process has lost contact with its servers.
B. The time is authoritative because the clock is in sync.
C. The clock is out of sync.
D. NTP is configured incorrectly.
E. The time is not authoritative.
Correct Answer: A
QUESTION 7
When a company puts a security policy in place, what is the effect on the company’s business?
A. Minimizing risk
B. Minimizing total cost of ownership
C. Minimizing liability
D. Maximizing compliance
Correct Answer: A
QUESTION 8
What is the purpose of the Integrity component of the CIA triad?
A. to ensure that only authorized parties can modify data
B. to determine whether data is relevant
C. to create a process for accessing data
D. to ensure that only authorized parties can view data
Correct Answer: A
QUESTION 9
Which feature of the Cisco Email Security Appliance can mitigate the impact of snowshoe spam and sophisticated phishing attacks?
A. contextual analysis
B. holistic understanding of threats
C. graymail management and filtering
D. signature-based IPS
Correct Answer: A
QUESTION 10
Which Cisco product can help mitigate web-based attacks within a network?
A. Adaptive Security Appliance
B. Web Security Appliance
C. Email Security Appliance
D. Identity Services Engine
Correct Answer: B
QUESTION 11
How can the administrator enable permanent client installation in a Cisco AnyConnect VPN firewall configuration?
A. Issue the command anyconnect keep-installer under the group policy or username webvpn mode
B. Issue the command anyconnect keep-installer installed in the global configuration
C. Issue the command anyconnect keep-installer installed under the group policy or username webvpn mode
D. Issue the command anyconnect keep-installer installer under the group policy or username webvpn mode
Correct Answer: C
QUESTION 12
In which three cases does the ASA firewall permit inbound HTTP GET requests during normal operations? 210-260 dumps (Choose three).
A. when matching NAT entries are configured
B. when matching ACL entries are configured
C. when the firewall receives a SYN-ACK packet
D. when the firewall receives a SYN packet
E. when the firewall requires HTTP inspection
F. when the firewall requires strict HTTP inspection
Correct Answer: ABD
Reference: https://www.leads4pass.com/210-260.html dumps exam training materials update free shared, the latest Cisco CCNA Security 210-260 dumps pdf training resources which are the best for clearing 210-260 test.
Latest Cisco CCNA Security 210-260 dumps vce youtube demo: https://youtu.be/seDmEyXcd3w

