The latest CompTIA CAS-003 dumps by leads4pass helps you pass the CAS-003 exam for the first time! leads4pass Latest Update CompTIA CAS-003 VCE Dump and CAS-003 PDF Dumps, leads4pass CAS-003 Exam Questions Updated, Answers corrected! Get the latest LeadPass CAS-003 dumps with Vce and PDF: https://www.leads4pass.com/cas-003.html (Q&As: 553 dumps)
[Free CAS-003 PDF] CompTIA CAS-003 Dumps PDF can be collected on Google Drive shared by leads4pass:
https://drive.google.com/file/d/1fNY0_NEfl5VS99bk_G7WM8YlshSfLth2/
[leads4pass CAS-003 Youtube] CompTIA CAS-003 Dumps can be viewed on Youtube shared by leads4pass
CompTIA CAS-003 Online Exam Practice Questions
QUESTION 1
After a security incident, an administrator would like to implement policies that would help reduce fraud and the potential
for collusion between employees. Which of the following would help meet these goals by having co-workers
occasionally audit another worker\\’s position?
A. Least privilege
B. Job rotation
C. Mandatory vacation
D. Separation of duties
Correct Answer: B
Job rotation can reduce fraud or misuse by preventing an individual from having too much control over an area.
QUESTION 2
The government is concerned with remote military missions being negatively being impacted by the use of technology
that may fail to protect operational security. To remediate this concern, a number of solutions have been implemented,
including the following:
End-to-end encryption of all inbound and outbound communication, including personal email and chat sessions that
allow soldiers to securely communicate with families. Layer 7 inspection and TCP/UDP port restriction, including firewall
rules to only allow TCP port 80 and 443 and approved applications A host-based whitelist of approved websites and
applications that only allow mission-related tools and sites The use of satellite communication to include multiple proxy
servers to scramble the source IP address
Which of the following is of MOST concern in this scenario?
A. Malicious actors intercepting inbound and outbound communication to determine the scope of the mission
B. Family members posting geotagged images on social media that were received via email from soldiers
C. The effect of communication latency that may negatively impact real-time communication with mission control
D. The use of centrally managed military network and computers by soldiers when communicating with external parties
Correct Answer: A
QUESTION 3
An investigation showed a worm was introduced from an engineer\\’s laptop. It was determined the company does not
provide engineers with company-owned laptops, which would be subject to a company policy and technical controls.
Which of the following would be the MOST secure control implement?
A. Deploy HIDS on all engineer-provided laptops, and put a new router in the management network.
B. Implement role-based group policies on the management network for client access.
C. Utilize a jump box that is only allowed to connect to client from the management network.
D. Deploy a company-wide approved engineering workstation for management access.
Correct Answer: A
QUESTION 4
Following a recent network intrusion, a company wants to determine the current security awareness of all of its
employees. Which of the following is the BEST way to test awareness?
A. Conduct a series of security training events with comprehensive tests at the end
B. Hire an external company to provide an independent audit of the network security posture
C. Review the social media of all employees to see how much proprietary information is shared
D. Send an email from a corporate account, requesting users to log onto a website with their enterprise account
Correct Answer: B
QUESTION 5
A security technician is incorporating the following requirements in an RFP for a new SIEM:
New security notifications must be dynamically implemented by the SIEM engine The SIEM must be able to identify
traffic baseline anomalies Anonymous attack data from all customers must augment attack detection and risk scoring
Based on the above requirements, which of the following should the SIEM support? (Choose two.)
A. Autoscaling search capability
B. Machine learning
C. Multisensor deployment
D. Big Data analytics
E. Cloud-based management
F. Centralized log aggregation
Correct Answer: BD
QUESTION 6
An information security officer is responsible for one secure network and one office network. Recent intelligence
suggests there is an opportunity for attackers to gain access to the secure network due to similar login credentials
across networks. To determine the users who should change their information, the information security officer uses a tool to scan a file with hashed values on both networks and receives the following data: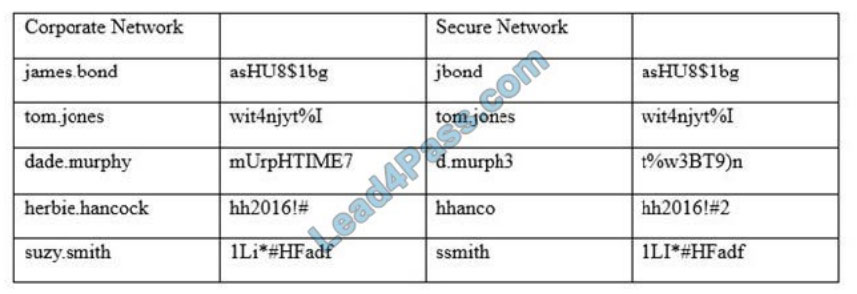
Which of the following tools was used to gather this information from the hashed values in the file?
A. Vulnerability scanner
B. Fuzzer
C. MD5 generator
D. Password cracker
E. Protocol analyzer
Correct Answer: C
QUESTION 7
A security administrator adding a NAC requirement for all VPN users to ensure the connecting devices are compliant
with company policy. Which of the following items provides the HIGHEST assurance to meet this requirement?
A. Implement a permanent agent.
B. Install antivirus software.
C. Use an agentless implementation.
D. Implement PKI.
Correct Answer: D
QUESTION 8
Ann, a systems engineer, is working to identify an unknown node on the corporate network. To begin her investigative
work, she runs the following Nmap command string: user@hostname:~$ Sudo Nmap 192.168.1.54 Based on the output,
Nmap is unable to identify the OS running on the node, but the following ports are open on the device: TCP/22 TCP/111
TCP/512-514 TCP/2049 TCP/32778 Based on this information, which of the following operating systems is MOST likely
running on the unknown node?
A. Linux
B. Windows
C. Solaris
D. OSX
Correct Answer: C
TCP/22 is used for SSH; TCP/111 is used for Sun RPC; TCP/512-514 is used by CMD like exec, but automatic
authentication is performed as with a login server, etc. These are all ports that are used when making use of the Sun
Solaris operating system.
QUESTION 9
A firm\\’s Chief Executive Officer (CEO) is concerned that the IT staff lacks the knowledge to identify complex vulnerabilities
that may exist in a payment system being internally developed. The payment system being developed will be sold to a
number of organizations and is in direct competition with another leading product. The CEO highlighted that code base
confidentiality is of critical importance to allow the company to exceed the competition in terms of the product\\’s
reliability, stability, and performance. Which of the following would provide the MOST thorough testing and satisfy the
CEO\\’s requirements?
A. Sign an MOU with a marketing firm to preserve the company reputation and use in-house resources for random
testing.
B. Sign a BPA with a small software consulting firm and use the firm to perform Black box testing and address all
findings.
C. Sign an NDA with a large security consulting firm and use the firm to perform Grey box testing and address all
findings.
D. Use the most qualified and senior developers on the project to perform a variety of White box testing and code
reviews.
Correct Answer: C
Gray box testing has limited knowledge of the system as an attacker would. The base code would remain confidential.
This would further be enhanced by a Non-disclosure agreement (NDA) which is designed to protect confidential
information.
QUESTION 10
The director of sales asked the development team for some small changes to increase the usability of an application
used by the sales team. Prior security reviews of the code showed no significant vulnerabilities, and since the changes
were small, they were given a peer review and then pushed to the live environment. Subsequent vulnerability scans now
show numerous flaws that were not present in the previous versions of the code. Which of the following is an SDLC best
practice that should have been followed?
A. Versioning
B. Regression testing
C. Continuous integration
D. Integration testing
Correct Answer: B
QUESTION 11
A penetration tester has been contracted to conduct a physical assessment of a site. Which of the following is the
MOST plausible method of social engineering to be conducted during this engagement?
A. Randomly calling customer employees and posing as a help desk technician requiring user password to resolve
issues
B. Posing as a copier service technician and indicating the equipment had “phoned home” to alert the
C. technician for a service call
D. Simulating an illness while at a client location for a sales call and then recovering once listening devices are installed
E. Obtaining fake government credentials and impersonating law enforcement to gain access to a company facility
Correct Answer: A
QUESTION 12
A company recently implemented a new cloud storage solution and installed the required synchronization client on all
company devices. A few months later, a breach of sensitive data was discovered. Root cause analysis shows the data breach happened from a lost personal mobile device.
Which of the following controls can the organization implement to reduce the risk of similar breaches?
A. Biometric authentication
B. Cloud storage encryption
C. Application containerization
D. Hardware anti-tamper
Correct Answer: A
QUESTION 13
A security policy states that all applications on the network must have a password length of eight characters. There are
three legacy applications on the network that cannot meet this policy. One system will be upgraded in six months, and
two are not expected to be upgraded or removed from the network. Which of the following processes should be
followed?
A. Establish a risk matrix
B. Inherit the risk for six months
C. Provide a business justification to avoid the risk
D. Provide a business justification for a risk exception
Correct Answer: D
The Exception Request must include:
A description of the non-compliance.
The anticipated length of non-compliance (2-year maximum).
The proposed assessment of risk associated with non-compliance.
The proposed plan for managing the risk associated with non-compliance.
The proposed metrics for evaluating the success of risk management (if the risk is significant).
The proposed review date to evaluate progress toward compliance.
An endorsement of the request by the appropriate Information Trustee (VP or Dean).
latest updated CompTIA CAS-003 exam questions from the leads4pass CAS-003 dumps! 100% pass the CAS-003 exam! Download leads4pass CAS-003 VCE and PDF dumps: https://www.leads4pass.com/cas-003.html (Q&As: 553 dumps)
Get free CompTIA CAS-003 dumps PDF online: https://drive.google.com/file/d/1fNY0_NEfl5VS99bk_G7WM8YlshSfLth2/

