The latest updated Microsoft 98-367 exam dumps and free 98-367 exam practice questions and answers! Latest updates from leads4pass Microsoft 98-367 Dumps PDF and 98-367 Dumps VCE, leads4pass 98-367 exam questions updated and answers corrected!
Get the full Microsoft 98-367 dumps from https://www.leads4pass.com/98-367.html (VCE&PDF)
Latest 98-367 PDF for free
Share the Microsoft 98-367 Dumps PDF for free From leads4pass 98-367 Dumps part of the distraction collected on Google Drive shared by leads4pass
https://drive.google.com/file/d/1Lvpzg6HNAoOTSbZd3Y8R9OwDcXX9KVxA/
The latest updated Microsoft 98-367 Exam Practice Questions and Answers Online Practice Test is free to share from leads4pass (Q1-Q12)
QUESTION 1
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is
worth one point.
Hot Area: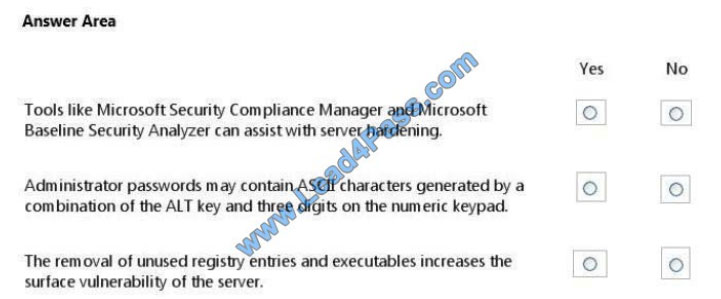
Correct Answer:

QUESTION 2
Role separation improves server security by:
A. Enforcing principle of least privilege.
B. Installing applications on separate hard disks.
C. Physically separating high-security servers from other servers.
D. Placing servers on separate VLANs.
Correct Answer: A
QUESTION 3
Mark works as a Network Administrator for Blue Well Inc. The company has a Windows-based network. Mark is facing a
series of problems with email spam and identifying theft via phishing scams. He wants to implement the various security
measures and to provide some education because it is related to the best practices while using email. Which of the
following will Mark ask employees of his company to do when they receive an email from a company they know with a
request to click the link to “verify their account information”?
A. Provide the required information
B. Hide the email
C. Use Read-only Domain Controller
D. Delete the email
Correct Answer: D
In the above scenario, Mark will ask his employees to delete the email whenever he receives an email from a company
that they know with to click the link to “verify their account information”, because companies do not ask for account
information via email nowadays.
Answer: C is incorrect. Read-only Domain Controller (RODC) is a domain controller that hosts the read-only partition of
the Active Directory database. RODC was developed by Microsoft typically to be deployed in a branch office
environment.
RODC is a good option to enhance security by placing it in a location where physical security is poor. RODC can also
be placed at locations having relatively few users and poor network bandwidth to the main site. As only the read-only
partition of the Active Directory database is hosted by RODC, a little local IT knowledge is required to maintain it.
QUESTION 4
Which of the following is a mechanism that allows authentication of dial-in and other network connections?
A. VPN
B. NTFS
C. RADIUS
D. Single Sign-On
Correct Answer: C
RADIUS is a mechanism that allows authentication of dial-in and other network connections. RADIUS is a client/server
protocol that runs in the application layer, using UDP as transport. The Remote Access Server, the Virtual Private Network server, the Network switch with port-based authentication, and the Network Access Server are all gateways
that control access to the network, and all have a RADIUS client component that communicates with the RADIUS
server. The RADIUS server is usually a background process running on a UNIX or Windows NT machine. RADIUS
serves three functions: To authenticate users or devices before granting them access to a network To authorize those
users or devices for certain network services To account for the usage of those services Answer: D is incorrect. Single sign-on is an approach that involves a server that acts as an online certificate authority within a single-sign-on system. A
single sign-on server will issue digital certificates into the client system, but never stores them. Users can execute
programs, etc. with the temporary certificate. It is common to find this solution variety with x.509-based certificates.
Answer: B is incorrect. NTFS is a high-performance file system proprietary to Microsoft. NTFS supports file-level
security, compression, and auditing. It also supports large volumes and powerful storage solutions such as RAID. The
latest feature of NTFS is its ability to encrypt files and folders to protect sensitive data. Answer: A is incorrect. A virtual
private network (VPN) is a form of wide-area network (WAN) that supplies network connectivity over a possibly long
physical distance. A virtual private network is a network that uses a public telecommunication infrastructure, such as the
Internet, to provide remote offices or individual users with secure access to their organization\\’s network. A virtual
private network can be contrasted with an expensive system of owned or leased lines that can only be used by one
organization. The goal of a VPN is to provide the organization with the same capabilities but at a much lower cost. A
VPN works by using the shared public infrastructure while maintaining privacy through security procedures and
tunneling protocols such as the Layer Two Tunneling Protocol (L2TP). In effect, the protocols, by encrypting data at the
sending end and decrypting it at the receiving end, send the data through a tunnel that cannot be entered by data that is
not properly encrypted. An additional level of security involves encrypting not only the data but also the originating and
receiving network addresses.
QUESTION 5
By default, what level of security is set for the Local intranet zone?
A. High-Medium
B. Medium-Low
C. High
D. Low
Correct Answer: B
The default security level of the Local intranet zone is Medium-Low. Internet Explorer (IE) allows configuring different
levels of security for different types of Web sites by segmenting them into the following security zone:
Local Intranet: IE can be configured to detect intranet sites automatically. Users can add Web sites to this zone through
Local Intranet sites dialog box. Protected Mode is not enabled for sites in this zone. The default security level of this
zone
is Medium-Low.
Trusted Sites: Putting sites in the Trusted Sites zone often provide elevated privileges. The default security level for this
zone is Medium. Restricted Sites: Potentially malicious sites are put in this zone. The default security level for this zone
is
High. Protected Mode is enabled by default for sites in this zone. Internet: The sites that are not contained in other
zones are automatically hosted in this zone. Sites in this zone are blocked from viewing private data from other Web. The default security level of this zone is Medium-High. Protected Mode is enabled by default for sites in this zone.
The three default security levels are Medium, Medium-High, and High.
QUESTION 6
You work as a Network Administrator for TechMart Inc. The company has a Windows-based network. After completing a
security audit of the company\\’s Microsoft Windows Server 2008 R2 file servers, you have determined that folder and
share security requires a revision on the basis of a corporate reorganization. You have noticed that some shares on the
file system are not secured. Which of the following is a feature that you will use to reassign permissions without
assigning permissions to every parent and child folder?
A. Inheritance
B. Kerberos
C. TCP/IP protocol
D. User Account Control (UAC)
Correct Answer: A
Inheritance is defined as the concept of permissions that are propagated to an object from a parent object. It is found in
both file system permissions and Active Directory permissions and does not work with share permissions. It is used to
reassign permissions without assigning permissions to every parent and child folder Answer: B is incorrect. Kerberos is
defined as a secure method used for authenticating a request for a service in a computer network. Answer: D is
incorrect. User Account Control (UAC) is used to prevent unauthorized changes to computers on the domain. Answer: C
is incorrect. TCP/IP protocol is used to define the rules computers are required to follow for communicating with each
other over the internet.
QUESTION 7
Which of the following is often used for one-to-many communications using broadcast or multicast IP datagrams?
A. UDP
B. FTP
C. HTTP
D. SMTP
Correct Answer: A
UDP is often used for one-to-many communications, using broadcast or multicast IP datagrams. User Datagram
Protocol (UDP) is one of the core members of the Internet Protocol Suite, the set of network protocols used for the
Internet. With UDP, computer applications can send messages, in this case, referred to as datagrams, to other hosts on
an Internet Protocol (IP) network without requiring prior communications to set up special transmission channels or data
paths. UDP is sometimes called the Universal Datagram Protocol. Answer: D is incorrect. Simple Mail Transfer Protocol
(SMTP) is a protocol for sending e-mail messages between servers. E-mailing systems use this protocol to send mails
over the Internet. SMTP works on the application layer of the TCP/IP or OSI reference model. The SMTP client typically
initiates a Transmission Control Protocol (TCP) connection to the SMTP server on the well-known port designated for
SMTP, port number 25. However, e-mail clients require POP or IMAP to retrieve mails from e-mail servers. Answer: B is
incorrect. File Transfer Protocol (FTP) is a standard network protocol used to copy a file from one host to another over a
TCP/IP-based network, such as the Internet. FTP is built on a client-server architecture and utilizes separate control
and data connections between the client and server applications, which solves the problem of different end-host
configurations (i.e., Operating System, file names). FTP is used with user-based password authentication or with
anonymous user access. Answer: C is incorrect. The HyperText Transfer Protocol is a standard application-level protocol used to request and transmit files, especially web pages and webpage components, on the World Wide Web.
HTTP runs on top of the TCP/IP protocol. Web browsers are HTTP clients that send file requests to Web Servers, which
in turn handle the requests via an HTTP service.
QUESTION 8
A malicious user who intercepts and modifies communications is known as a:
A. red hat hacker
B. white hat hacker
C. network sniffer
D. man-in-the-middle
Correct Answer: D
QUESTION 9
Which of the following is the process used by attackers for listening to the network traffic?
A. Eavesdropping
B. Subnetting
C. Sanitization
D. Hacking
Correct Answer: A
Eavesdropping is the process of listening to private conversations. It also includes attackers listening to the network traffic.
For example, it can be done over telephone lines (wiretapping), email, instant messaging, and any other method of
communication considered private.
Answer: C is incorrect. Sanitization is the process of removing sensitive information from a document or other medium
so that it may be distributed to a broader audience. When dealing with classified information, sanitization attempts to
reduce the document\\’s classification level, possibly yielding an unclassified document. Originally, the term sanitization
was applied to printed documents; it has since been extended to apply to computer media and the problem of data
remanence as well.
Answer: D is incorrect. Hacking is a process by which a person acquires illegal access to a computer or network through a security break or by implanting a virus on the computer or network.
Answer: B is incorrect. Subnetting is a process through which an IP address network is divided into smaller networks. It
is a hierarchical partitioning of the network address space of an organization into several subnets. Subnetting creates
smaller broadcast domains. It helps in the better utilization of the bits in the Host ID.
QUESTION 10
You manage 50 Windows workstations in a computer lab. All workstations belong to the lab Active Directory domain.
You need to implement several audit policies on each workstation in the shortest time possible.
What should you do?
A. Enable logging on each computer
B. Create a domain Group Policy
C. Turn on the Audit Policy on the domain controller
D. Enable Audit object access
Correct Answer: B
References:
https://docs.microsoft.com/en-us/windows-server/networking/branchcache/deploy/use-group-policy-to-configure-domainmember-client-computers
QUESTION 11
This question requires that you evaluate the underlined text to determine if it is correct.
Malware is any kind of unwanted software that is installed without your consent.
Instructions: Review the underlined text. If it makes the statement correct, select “No change is needed”. If the
statement is incorrect, select the answer choice that makes the statement correct.
A. Trojans are
B. Worms are
C. Viruses are
D. No change is needed
Correct Answer: D
QUESTION 12
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is
worth one point.
Hot Area:
Correct Answer:

Fulldumps shares the latest updated Microsoft 98-367 exam exercise questions, 98-367 dumps pdf for free.
All exam questions and answers come from the leads4pass exam dumps shared part! leads4pass updates throughout the year and shares a portion of your exam questions for free to help you understand the exam content and enhance your exam experience!
Get the full Microsoft 98-367 exam dumps questions at: https://www.leads4pass.com/98-367.html (pdf&vce)
ps.
Get free Microsoft 98-367 dumps PDF online: https://drive.google.com/file/d/1Lvpzg6HNAoOTSbZd3Y8R9OwDcXX9KVxA/

