The latest updated Microsoft az-500 exam dumps and free az-500 exam practice questions and answers! Latest updates from leads4pass Microsoft az-500 Dumps PDF and az-500 Dumps VCE, leads4pass az-500 exam questions updated and answers corrected!
Get the full Microsoft az-500 dumps from https://www.leads4pass.com/az-500.html (VCE&PDF)
Latest az-500 PDF for free
Share the Microsoft az-500 Dumps PDF for free From leads4pass az-500 Dumps part of the distraction collected on Google Drive shared by leads4pass
https://drive.google.com/file/d/12-RJDaQX5B8Xb9ZalvpgnjZekSGjleXS/
Latest leads4pass az-500 Youtube
Share the latest Microsoft az-500 exam practice questions and answers for free from Led4Pass Dumps viewed online by Youtube Videos
The latest updated Microsoft az-500 Exam Practice Questions and Answers Online Practice Test is free to share from leads4pass (Q1-Q13)
QUESTION 1
You need to meet the identity and access requirements for Group1. What should you do?
A. Add a membership rule to Group1.
B. Delete Group1. Create a new group named Group1 that has a membership type of Office 365. Add users and
devices to the group.
C. Modify the membership rule of Group1.
D. Change the membership type of Group1 to Assigned. Create two groups that have dynamic memberships. Add the
new groups to Group1.
Correct Answer: B
Incorrect Answers:
A, C: You can create a dynamic group for devices or for users, but you can\\’t create a rule that contains both users and
devices.
D: For an assigned group, you can only add individual members.
Scenario:
Litware identifies the following identity and access requirements: All San Francisco users and their devices must be
members of Group1.
The tenant currently contains this group: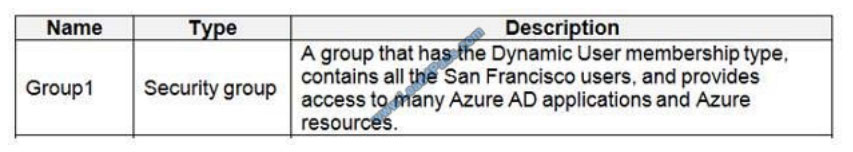
References: https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/groups-dynamic-membership
https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/active-directory-groups-create-azure-portal
QUESTION 2
You have 10 virtual machines on a single subnet that has a single network security group (NSG).
You need to log the network traffic to an Azure Storage account.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Install the Network Performance Monitor solution.
B. Enable Azure Network Watcher.
C. Enable diagnostic logging for the NSG.
D. Enable NSG flow logs.
E. Create an Azure Log Analytics workspace.
Correct Answer: BD
A network security group (NSG) enables you to filter inbound traffic to, and outbound traffic from, a virtual machine
(VM). You can log network traffic that flows through an NSG with Network Watcher\\’s NSG flow log capability. Steps
include: Create a VM with a network security group Enable Network Watcher and register the Microsoft.Insights provider
Enable a traffic flow log for an NSG, using Network Watcher\\’s NSG flow log capability Download logged data View
logged data
Reference: https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-nsg-flow-logging-portal
QUESTION 3
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains
a unique solution that might meet the stated goals. Some question sets might have more than one correct solution,
while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not
appear on the review screen.
You have an Azure Subscription named Sub1.
You have an Azure Storage account named Sa1 in a resource group named RG1.
Users and applications access the blob service and the file service in Sa1 by using several shared access signatures
(SASs) and stored access policies.
You discover that unauthorized users accessed both the file service and the blob service.
You need to revoke all access to Sa1.
Solution: You generate new SASs.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
Instead, you should create a new stored access policy.
To revoke a stored access policy, you can either delete it or rename it by changing the signed identifier. Changing the
signed identifier breaks the associations between any existing signatures and the stored access policy. Deleting or
renaming the stored access policy immediately affects all of the shared access signatures associated with it.
References: https://docs.microsoft.com/en-us/rest/api/storageservices/Establishing-a-Stored-Access-Policy
QUESTION 4
You have an Azure Container Registry named Registry1.
You add role assignment for Registry1 as shown in the following table.
Which users can upload images to Registry1 and download images from Registry1? To answer, select the appropriate
options in the answer area. NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
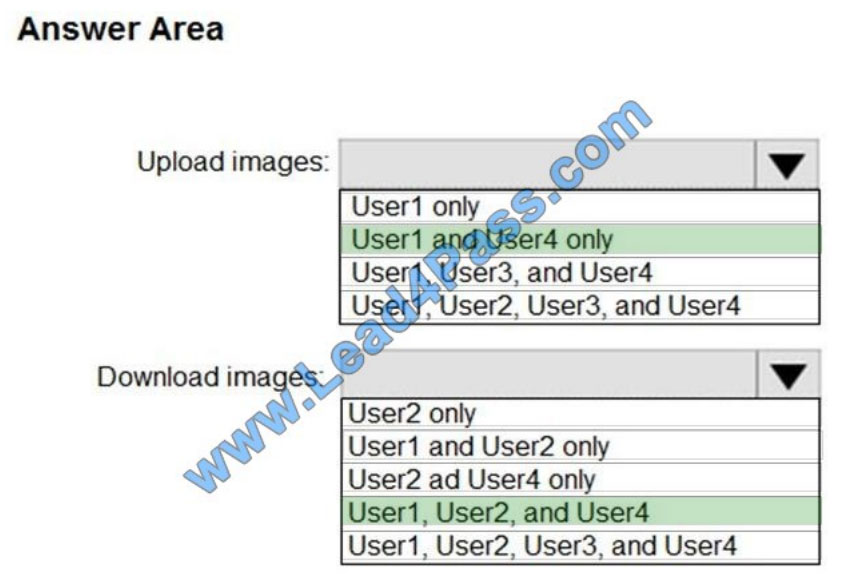
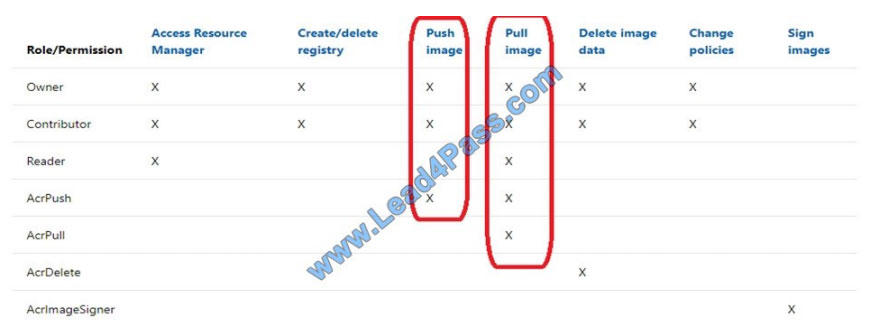
Box 1: User1 and User4 only
Owner, Contributor, and AcrPush can push images.
Box 2: User1, User2, and User4
All, except AcrImagineSigner, can download/pull images.
References: https://docs.microsoft.com/bs-latn-ba/azure/container-registry/container-registry-roles
QUESTION 5
You need to create an Azure key vault. The solution must ensure that any object deleted from the key vault be retained
for 90 days.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: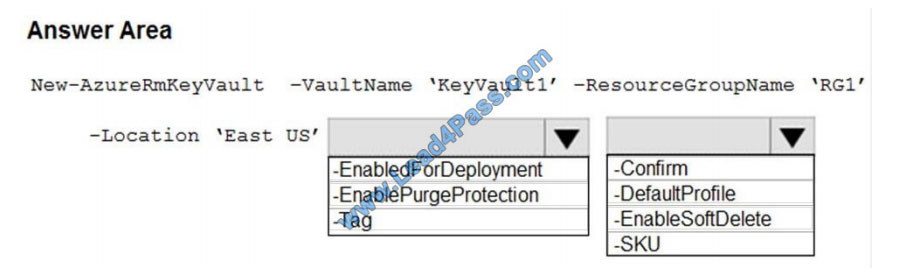
Correct Answer:
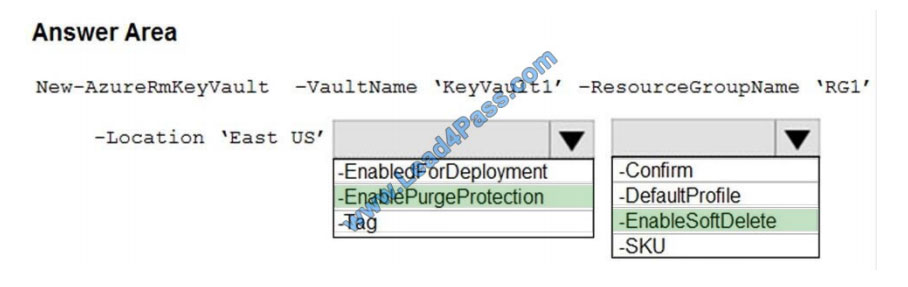
Box 1: -EnablePurgeProtection
If specified, protection against immediate deletion is enabled for this vault; requires soft delete to be enabled as well.
Box 2: -EnableSoftDelete
Specifies that the soft-delete functionality is enabled for this key vault. When soft-delete is enabled, for a grace period,
you can recover this key vault and its contents after it is deleted.
References:
https://docs.microsoft.com/en-us/powershell/module/azurerm.keyvault/new-azurermkeyvault
QUESTION 6
Exhibit tab.)
You are testing an Azure Kubernetes Service (AKS) cluster. The cluster is configured as shown in the exhibit. (Click the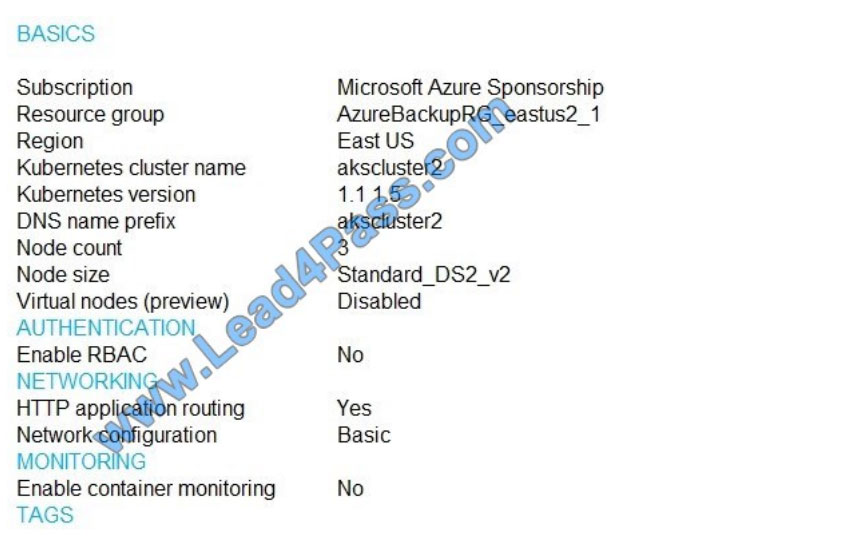
You plan to deploy the cluster to production. You disable HTTP application routing.
You need to implement application routing that will provide reverse proxy and TLS termination for AKS services by using
a single IP address.
What should you do?
A. Create an AKS Ingress controller.
B. Install the container network interface (CNI) plug-in.
C. Create an Azure Standard Load Balancer.
D. Create an Azure Basic Load Balancer.
Correct Answer: A
An ingress controller is a piece of software that provides reverse proxy, configurable traffic routing, and TLS termination
for Kubernetes services.
References: https://docs.microsoft.com/en-us/azure/aks/ingress-tls
QUESTION 7
You create a new Azure subscription.
You need to ensure that you can create custom alert rules in Azure Security Center.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Onboard Azure Active Directory (Azure AD) Identity Protection.
B. Create an Azure Storage account.
C. Implement Azure Advisor recommendations.
D. Create an Azure Log Analytics workspace.
E. Upgrade the pricing tier of Security Center to Standard.
Correct Answer: BD
D: You need to write permission in the workspace that you select to store your custom alert.
References: https://docs.microsoft.com/en-us/azure/security-center/security-center-custom-alert
QUESTION 8
You have an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains the users shown in the
following table.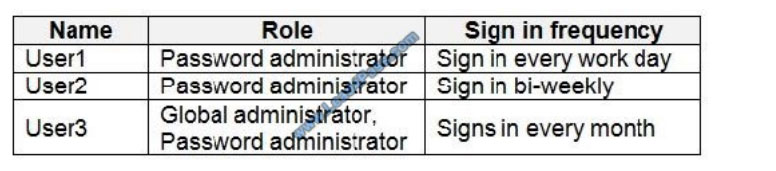
You configure an access review named Review1 as shown in the following exhibit.
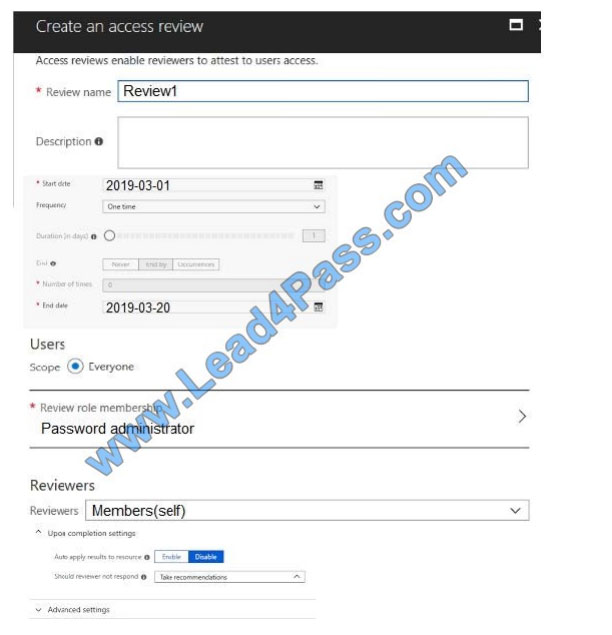
Use the drop-down menus to select the answer choice that completes each statement based on the information
presented in the graphic. NOTE: Each correct selection is worth one point.
Hot Area:
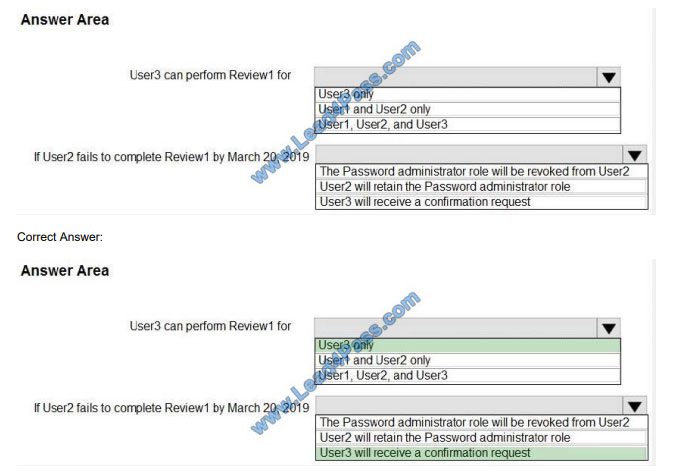
Box 1: User3 only
Use the Members (self) option to have the users review their own role assignments.
Box 2: User3 will receive a confirmation request
Use the Should reviewer not respond list to specify what happens for users that are not reviewed by the reviewer within
the review period. This setting does not impact users who have been reviewed by the reviewers manually. If the final
reviewer\\’s decision is Deny, then the user\\’s access will be removed.
No change – Leave user\\’s access unchanged
Remove access – Remove user\\’s access
Approve access – Approve user\\’s access
Take recommendations – Take the system\\’s recommendation on denying or approving the user\\’s continued access
References:
https://docs.microsoft.com/bs-latn-ba/azure/active-directory/privileged-identity-management/pim-how-to-start-securityreview
QUESTION 9
You need to ensure that User2 can implement PIM. What should you do first?
A. Assign User2 the global administrator role.
B. Configure authentication methods for contoso.com.
C. Configure the identity secure score for contoso.com.
D. Enable multi-factor authentication (MFA) for User2.
Correct Answer: A
To start using PIM in your directory, you must first enable PIM.
1. Sign in to the Azure portal as a Global Administrator of your directory.
You must be a Global Administrator with an organizational account (for example, @yourdomain.com), not a Microsoft
account (for example, @outlook.com), to enable PIM for a directory.
Scenario: Technical requirements include: Enable Azure AD Privileged Identity Management (PIM) for contoso.com
References:
https://docs.microsoft.com/bs-latn-ba/azure/active-directory/privileged-identity-management/pim-getting-started
QUESTION 10
You assign User8 the Owner role for RG4, RG5, and RG6.
In which resource groups can User8 create virtual networks and NSGs? To answer, select the appropriate options in the
answer area.
NOTE: Each correct selection is worth one point.
Hot Area: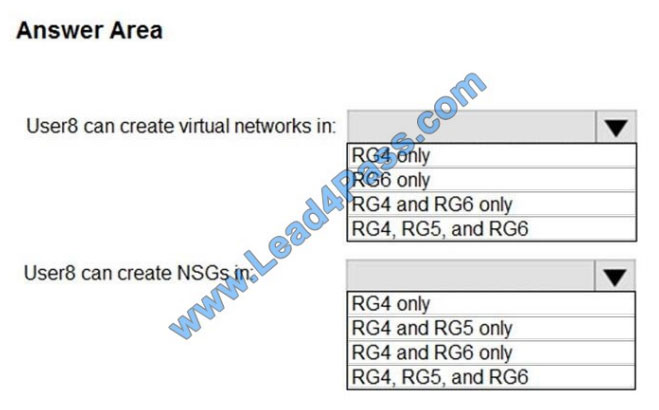
Correct Answer:
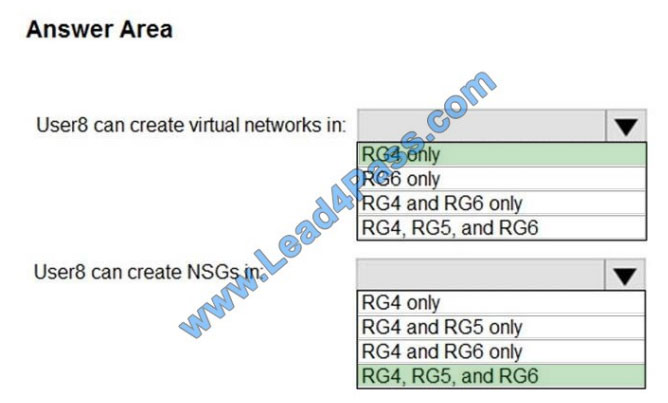
Box 1: RG4 only
Virtual Networks are not allowed for Rg5 and Rg6.
Box 2: Rg4, Rg5, and Rg6
Scenario:
Contoso has two Azure subscriptions named Sub1 and Sub2.
Sub1 contains six resource groups named RG1, RG2, RG3, RG4, RG5, and RG6.
You assign User8 the Owner role for RG4, RG5, and RG6
User8 city Sidney, Role: None
Note: A network security group (NSG) contains a list of security rules that allow or deny network traffic to resources
connected to Azure Virtual Networks (VNet). NSGs can be associated with subnets, individual VMs (classic), or individual
network interfaces (NIC) attached to VMs (Resource Manager).
References:
https://docs.microsoft.com/en-us/azure/governance/policy/overview
QUESTION 11
You need to configure SQLDB1 to meet the data and application requirements.
Which three actions should you recommend be performed in sequence? To answer, move the appropriate actions from
the list of actions to the answer area and arrange them in the correct order.
Select and Place: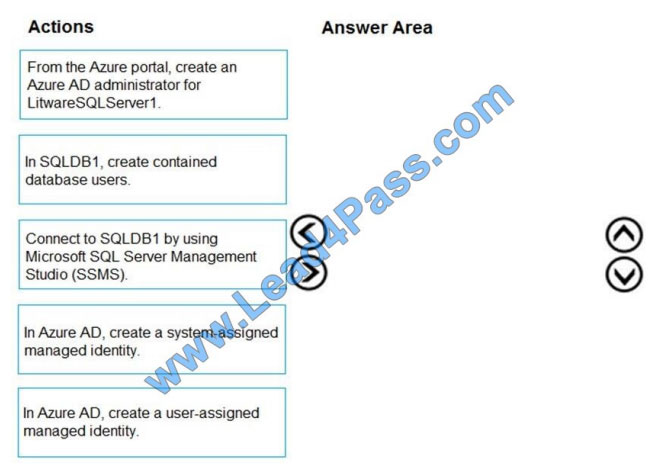
Correct Answer:
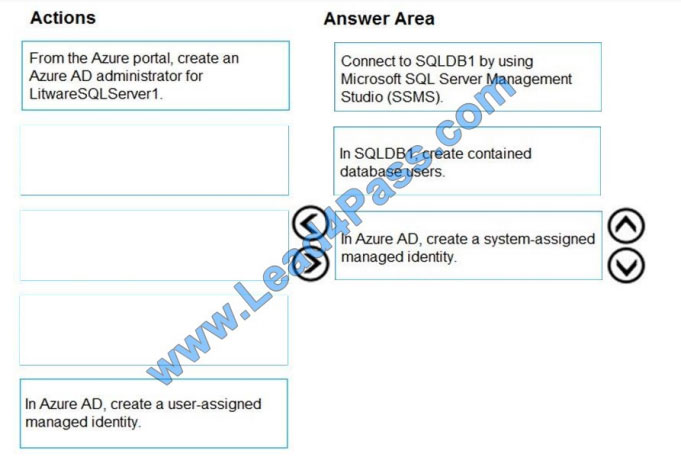
Step 1: Connect to SQLDB1 by using Microsoft SQL Server Management Studio (SSMS)
Step 2: In SQLDB1, create contained database users.
Create a contained user in the database that represents the VM\\’s system-assigned identity.
Step 3: In Azure AD, create a system-assigned managed identity.
A system-assigned identity for a Windows virtual machine (VM) can be used to access an Azure SQL server. Managed
Service Identities are automatically managed by Azure and enable you to authenticate to services that support Azure
AD
authentication, without needing to insert credentials into your code.
References:
https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/tutorial-windows-vm-accesssql
QUESTION 12
You have an Azure subscription named Sub1. Sub1 contains an Azure virtual machine named VM1 that runs Windows
Server 2016.
You need to encrypt VM1 disks by using Azure Disk Encryption.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions
to the answer area and arrange them in the correct order.
Select and Place: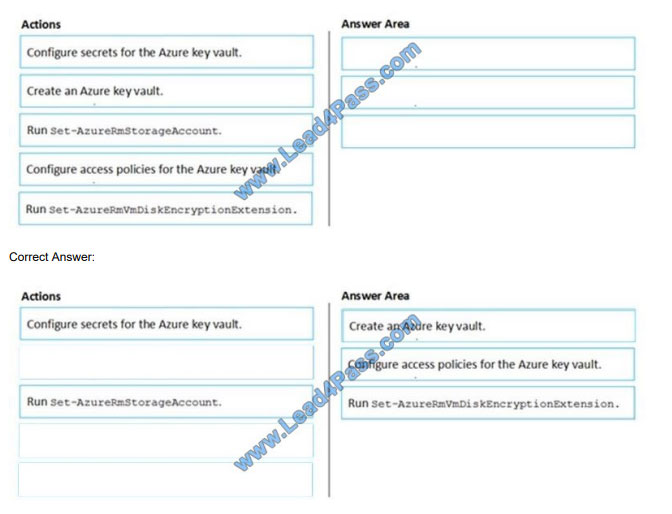
References: https://docs.microsoft.com/en-us/azure/virtual-machines/windows/encrypt-disks
QUESTION 13
You suspect that users are attempting to sign in to resources to which they have no access.
You need to create an Azure Log Analytics query to identify failed user sign-in attempts from the last three days. The
results must only show users who had more than five failed sign-in attempts.
How should you configure the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: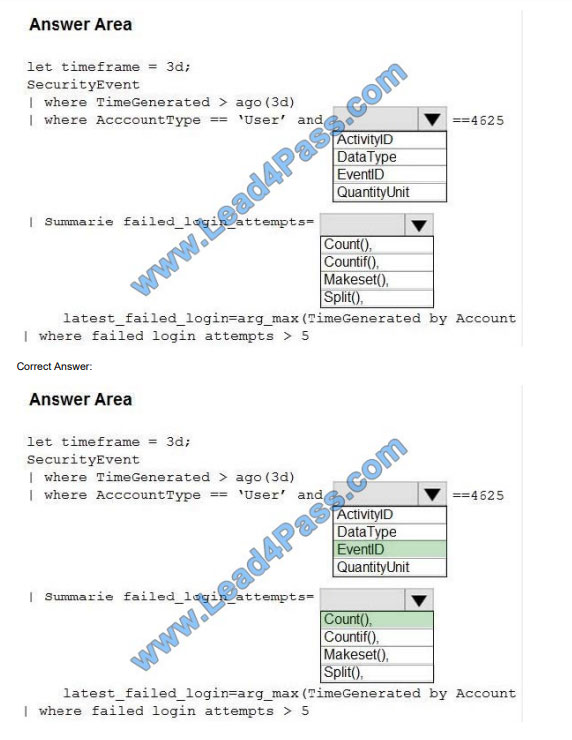
The following example identifies user accounts that failed to log in more than five times in the last day, and when they
last attempted to log in.
let timeframe = 1d; SecurityEvent | where TimeGenerated > ago(1d) | where AccountType == \\’User\\’ and EventID ==
4625 // 4625 – failed log in | summarize failed_login_attempts=count(), latest_failed_login=arg_max(TimeGenerated,
Account) by Account | where failed_login_attempts > 5 | project-away Account1
References: https://docs.microsoft.com/en-us/azure/azure-monitor/log-query/examples
Fulldumps shares the latest updated Microsoft az-500 exam exercise questions, az-500 dumps pdf, and Youtube video learning for free.
All exam questions and answers come from the leads4pass exam dumps shared part! leads4pass updates throughout the year and shares a portion of your exam questions for free to help you understand the exam content and enhance your exam experience!
Get the full Microsoft az-500 exam readiness dumps questions at https://www.leads4pass.com/az-500.html (pdf&vce)
ps.
Get free Microsoft az-500 dumps PDF online: https://drive.google.com/file/d/12-RJDaQX5B8Xb9ZalvpgnjZekSGjleXS/

