2018 new Cisco CCNA Cyber Ops 210-250 dumps exam training resources in PDF format free download from leads4pass. The best useful Cisco CCNA Cyber Ops 210-250 dumps pdf materials and vce youtube demo update free shared. “Understanding Cisco Cybersecurity Fundamentals” is the name of 210-250 SECFND Cisco exam dumps which covers all the knowledge points of the real Cisco exam. If you want to get success with good grades then these Cisco CCNA Cyber Ops 210-250 dumps exam question answers are splendid platform for you I personally review this web many times that’s why I am suggesting you this one.
Useful latest Cisco CCNA Cyber Ops 210-250 dumps exam questions and answers download free try. Get your Cisco CCNA Cyber Ops 210-250 dumps exam preparation questions in form of 210-250 PDF. Download Cisco CCNA Cyber Ops real leads4pass 210-250 dumps exam questions and verified answers. 100% passing guarantee and full refund in case of failure.
Vendor: Cisco
Certifications: CCNA Cyber Ops
Exam Name: Understanding Cisco Cybersecurity Fundamentals
Exam Code: 210-250
Total Questions: 80 Q&As
New Cisco CCNA Cyber Ops 210-250 Dumps Exam Questions And Answers (1-30)
QUESTION 1
Which two protocols are used for email (Choose two )
A. NTP
B. DNS
C. HTTP
D. IMAP
E. SMTP
Correct Answer: DE
QUESTION 2
At which OSI layer does a router typically operate?
A. Transport
B. Network
C. Data link
D. Application
Correct Answer: B
QUESTION 3
While viewing packet capture data, you notice that one IP is sending and receiving traffic for multiple devices by modifying the IP header, Which option is making this behavior possible?
A. TOR
B. NAT
C. encapsulation
D. tunneling
Correct Answer: B
QUESTION 4
Which option is a purpose of port scanning?
A. Identify the Internet Protocol of the target system.
B. Determine if the network is up or down
C. Identify which ports and services are open on the target host.
D. Identify legitimate users of a system.
Correct Answer: C
QUESTION 5
An intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources. Which evasion technique does this attempt indicate?
A. traffic fragmentation
B. resource exhaustion
C. timing attack
D. tunneling
Correct Answer: B
QUESTION 6
Which two activities are examples of social engineering? (Choose two)
A. receiving call from the IT department asking you to verify your username/password to maintain the account
B. receiving an invite to your department’s weekly WebEx meeting
C. sending a verbal request to an administrator to change the password to the account of a user the administrator does know
D. receiving an email from MR requesting that you visit the secure HR website and update your contract information
E. receiving an unexpected email from an unknown person with an uncharacteristic attachment from someone in the same company
Correct Answer: AC
QUESTION 7
Cisco pxGrid has a unified framework with an open API designed in a hub-and-spoke architecture. pxGrid is used to enable the sharing of contextual-based information from which devices?
A. From a Cisco ASA to the Cisco OpenDNS service
B. From a Cisco ASA to the Cisco WSA
C. From a Cisco ASA to the Cisco FMC
D. From a Cisco ISE session directory to other policy network systems, such as Cisco IOS devices and the Cisco ASA
Correct Answer: D
QUESTION 8
Which definition of a daemon on Linux is true?
A. error check right after the call to fork a process
B. new process created by duplicating the calling process
C. program that runs unobtrusively in the background
D. set of basic CPU instructions
Correct Answer: C
QUESTION 9
A user reports difficulties accessing certain external web pages, When examining traffic to and from the external domain in full packet captures, you notice many SYNs that have the same sequence number, 210-250 dumps source, and destination IP address, but have different payloads.
Which problem is a possible explanation of this situation?
A. insufficient network resources
B. failure of full packet capture solution
C. misconfiguration of web filter
D. TCP injection
Correct Answer: D
QUESTION 10
Which definition describes the main purpose of a Security Information and Event Management solution ?
A. a database that collects and categorizes indicators of compromise to evaluate and search for potential security threats
B. a monitoring interface that manages firewall access control lists for duplicate firewall filtering
C. a relay server or device that collects then forwards event logs to another log collection device
D. a security product that collects, normalizes, and correlates event log data to provide holistic views of the security posture
Correct Answer: D
QUESTION 11
Which information security property is supported by encryption?
A. sustainability
B. integrity
C. confidentiality
D. availability
Correct Answer: C
QUESTION 12
Which term describes the act of a user, without authority or permission, obtaining rights on a system, beyond what were assigned?
A. authentication tunneling
B. administrative abuse
C. rights exploitation
D. privilege escalation
Correct Answer: D
QUESTION 13
Which definition of the IIS Log Parser tool is true?
A. a logging module for IIS that allows you to log to a database
B. a data source control to connect to your data source
C. a powerful, versatile tool that makes it possible to run SQL-like queries against log flies
D. a powerful versatile tool that verifies the integrity of the log files
Correct Answer: C
QUESTION 14
What are the advantages of a full-duplex transmission mode compared to half-duplex mode? (Select all that apply.)
A. Each station can transmit and receive at the same time.
B. It avoids collisions.
C. It makes use of backoff time.
D. It uses a collision avoidance algorithm to transmit.
Correct Answer: AB
QUESTION 15
Which term represents the chronological record of how evidence was collected- analyzed, preserved, and transferred?
A. chain of evidence
B. evidence chronology
C. chain of custody
D. record of safekeeping
Correct Answer: C
QUESTION 16
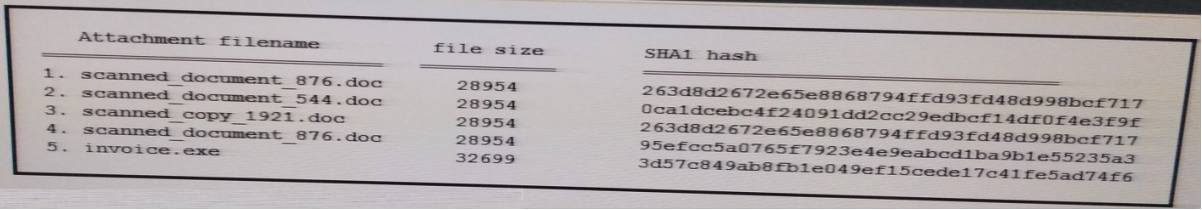
Refer to the exhibit. During an analysis this list of email attachments is found. Which files contain the same content?
A. 1 and 4
B. 3 and 4
C. 1 and 3
D. 1 and 2
Correct Answer: C
QUESTION 17
210-250 dumps In which case should an employee return his laptop to the organization?
A. When moving to a different role
B. Upon termination of the employment
C. As described in the asset return policy
D. When the laptop is end of lease
Correct Answer: C
QUESTION 18
A firewall requires deep packet inspection to evaluate which layer?
A. application
B. Internet
C. link
D. transport
Correct Answer: A
QUESTION 19
Which event occurs when a signature-based IDS encounters network traffic that triggers an alert?
A. connection event
B. endpoint event
C. NetFlow event
D. intrusion event
Correct Answer: D
QUESTION 20
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IPS phones?
A. replay
B. man-in-the-middle
C. dictionary
D. known-plaintext
Correct Answer: B
QUESTION 21
Which situation indicates application-level white listing?
A. Allow everything and deny specific executable files.
B. Allow specific executable files and deny specific executable files.
C. Writing current application attacks on a whiteboard daily.
D. Allow specific files and deny everything else.
Correct Answer: B
QUESTION 22
Which definition of an antivirus program is true?
A. program used to detect and remove unwanted malicious software from the system
B. program that provides real time analysis of security alerts generated by network hardware and application
C. program that scans a running application for vulnerabilities
D. rules that allow network traffic to go in and out
Correct Answer: A
QUESTION 23
Which of the following is true about heuristic-based algorithms?
A. Heuristic-based algorithms may require fine tuning to adapt to network traffic and minimize the possibility of false positives.
B. Heuristic-based algorithms do not require fine tuning.
C. Heuristic-based algorithms support advanced malware protection.
D. Heuristic-based algorithms provide capabilities for the automation of IPS signature creation and tuning.
Correct Answer: A
QUESTION 24
Which security principle states that more than one person is required to perform a critical task?
A. due diligence
B. separation of duties
C. need to know
D. least privilege
Correct Answer: B
QUESTION 25
Which tool is commonly used by threat actors on a webpage to take advantage of the software vulnerabilities of a system to spread malware?
A. exploit kit
B. root kit
C. vulnerability kit
D. script kiddie kit
Correct Answer: A
QUESTION 26
If a web server accepts input from the user and passes it to a bash shell, to which attack method is it vulnerable?
A. input validation
B. hash collision
C. command injection
D. integer overflow
Correct Answer: C
QUESTION 27
Based on which statement does the discretionary access control security model grant or restrict access ? 210-250 dumps
A. discretion of the system administrator
B. security policy defined by the owner of an object
C. security policy defined by the system administrator
D. role of a user within an organization
Correct Answer: B
QUESTION 28
Which definition of the virtual address space for a Windows process is true?
A. actual physical location of an object in memory
B. set of virtual memory addresses that it can use
C. set of pages that are currently resident in physical memory
D. system-level memory protection feature that is built into the operating system
Correct Answer: B
QUESTION 29
Which statement about digitally signing a document is true?
A. The document is hashed and then the document is encrypted with the private key.
B. The document is hashed and then the hash is encrypted with the private key.
C. The document is encrypted and then the document is hashed with the public key
D. The document is hashed and then the document is encrypted with the public key.
Correct Answer: B
QUESTION 30
You must create a vulnerability management framework. Which main purpose of this framework is true?
A. Conduct vulnerability scans on the network.
B. Manage a list of reported vulnerabilities.
C. Identify remove and mitigate system vulnerabilities.
D. Detect and remove vulnerabilities in source code.
Correct Answer: B
The Following Are Some Reviews From Our Customers:
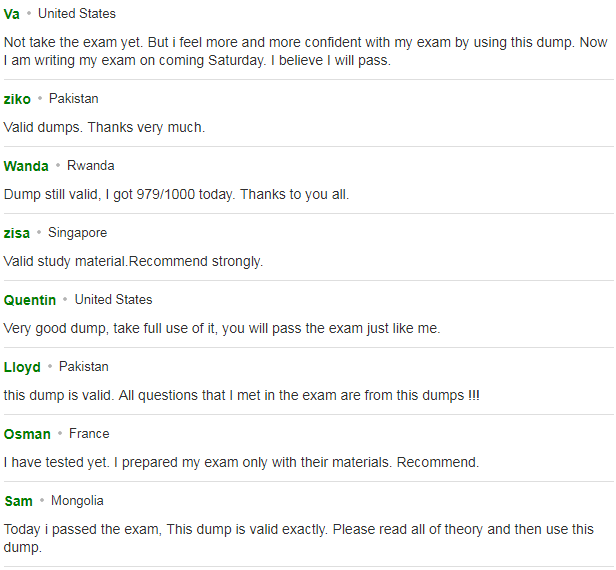
You can click here to have a review about us: https://www.resellerratings.com/store/leads4pass
Google drive Cisco 210-250 dumps pdf training resource: https://drive.google.com/open?id=0B_7qiYkH83VRaF8zb0JFVmRVclU
Google drive Cisco 210-255 dumps pdf training resource: https://drive.google.com/open?id=0B_7qiYkH83VRTTJsYkV3c2xZb2s
Why Lead 4 pass?
leads4pass is the best IT learning material provider. leads4pass is the number one choice among IT professionals, especially the ones who are looking to climb up the hierarchy levels faster in their respective organizations. Other brands appeared early, the questions are not the latest and it is very expensive. leads4pass provide the newest and cheapest questions and answers. leads4pass is the correct choice for IT learning materials, help you pass your exam easily.

Newest helpful Cisco CCNA Cyber Ops 210-250 dumps pdf practice files and study guides free download from leads4pass. The best and most updated latest Cisco CCNA Cyber Ops 210-250 dumps pdf training resources which are the best for clearing 210-250 exam test, and to get certified by Cisco CCNA Cyber Ops. Cisco CCNA Cyber Ops 210-250 dumps exam preparation kit contains all the necessary 210-250 questions that you need to know.
High quality Cisco CCNA Cyber Ops 210-250 dumps vce youtube:
https://youtu.be/YF5kWehwKzc

