The latest CompTIA cs0-001 dumps by leads4pass helps you pass the cs0-001 exam for the first time! leads4pass Latest Update CompTIA cs0-001 VCE Dump and cs0-001 PDF Dumps, leads4pass cs0-001 Exam Questions Updated, Answers corrected! Get the latest LeadPass cs0-001 dumps with Vce and PDF: https://www.leads4pass.com/cs0-001.html (Q&As: 416 dumps)
[Free cs0-001 PDF] CompTIA cs0-001 Dumps PDF can be collected on Google Drive shared by leads4pass:
https://drive.google.com/file/d/1MaCotAg3BQj1g1fidH-fZjbpFsyQftqh/
[leads4pass cs0-001 Youtube] CompTIA cs0-001 Dumps can be viewed on Youtube shared by leads4pass
CompTIA cs0-001 Online Exam Practice Questions
QUESTION 1
A technician receives a report that a user\\’s workstation is experiencing no network connectivity. The technician
investigates and notices the patch cable running the back of the user\\’s VoIP phone is routed directly under the rolling
chair and
has been smashed flat over time.
Which of the following is the most likely cause of this issue?
A. Cross-talk
B. Electromagnetic interference
C. Excessive collisions
D. Split pairs
Correct Answer: C
QUESTION 2
A zero-day crypto-worm is quickly spreading through the internal network on port 25 and exploiting a software
vulnerability found within the email servers. Which of the following countermeasures needs to be implemented as soon
as possible to mitigate the worm from continuing to spread?
A. Implement a traffic sinkhole.
B. Block all known port/services.
C. Isolate impacted servers.
D. Patch affected systems.
Correct Answer: C
QUESTION 3
A security analyst is conducting a vulnerability assessment of older SCADA devices on the corporate network. Which of
the following compensating controls are likely to prevent the scans from providing value?
A. Access control list network segmentation that prevents access to the SCADA devices inside the network.
B. Detailed and tested firewall rules that effectively prevent outside access of the SCADA devices.
C. Implementation of a VLAN that allows all devices on the network to see all SCADA devices on the network.
D. SCADA systems configured with `SCADA SUPPORT\\’=ENABLE
Correct Answer: B
QUESTION 4
A security team is implementing a new vulnerability management program in an environment that has a historically poor
security posture. The team is aware of issues patch management in the environment and expects a large number of
findings. Which of the following would be the MOST efficient way to increase the security posture of the organization in
the shortest amount of time?
A. Create an SLA stating that remediation actions must occur within 30 days of discovery for all levels of vulnerabilities.
B. Incorporate prioritization levels into the remediation process and address critical findings first.
C. Create classification criteria for data residing on different servers and provide remediation only for servers housing
sensitive data.
D. Implement a change control policy that allows the security team to quickly deploy patches in the production
environment to reduce the risk of any vulnerabilities found.
Correct Answer: B
QUESTION 5
A security architect is reviewing the options for performing input validation on incoming web form submissions. Which of
the following should the architect as the MOST secure and manageable option?
A. Client-side whitelisting
B. Server-side whitelisting
C. Server-side blacklisting
D. Client-side blacklisting
Correct Answer: B
QUESTION 6
An organization is conducting penetration testing to identify possible network vulnerabilities. The penetration tester has
received the following output from the latest scan: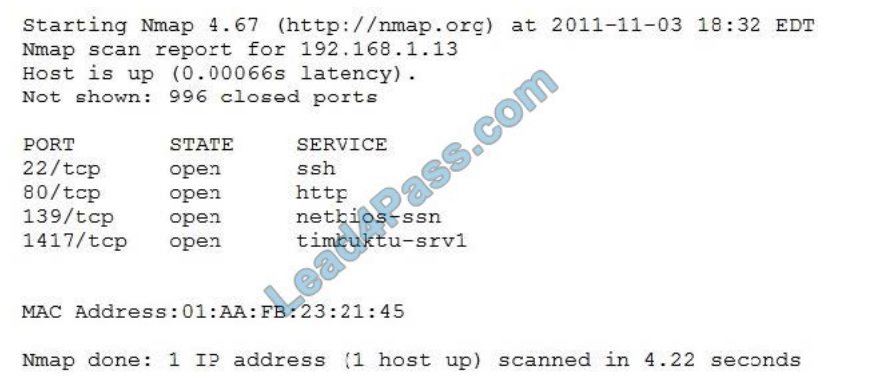
The penetration tester knows the organization does not use Timbuktu servers and wants to have Nmap interrogate the
ports on the target in more detail. Which of the following commands should the penetration tester use NEXT?
A. nmap ?V 192.168.1.13 ?1417
B. nmap ?S 192.168.1.13 ?1417
C. sudo Nmap ?S 192.168.1.13
D. Nmap 192.168.1.13?
Correct Answer: A
QUESTION 7
A cybersecurity analyst was asked to review several results of web vulnerability scan logs.
Given the following snippet of code:
Which of the following BEST describes the situation and recommendations to be made?
A. The security analyst has discovered an embedded iframe pointing to source IP 65.240.22.1 network. The code
should include the domain name. Recommend the entry be updated with the domain name.
B. The security analyst has discovered an embedded iframe that is hidden from users accessing the web page. This
code is correct. This is a design preference, and no vulnerabilities are present.
C. The security analyst has discovered an embedded iframe pointing to source IP 65.240.22.1 network. The link is
hidden and suspicious. Recommend the entry be removed from the web page.
D. The security analyst has discovered an embedded iframe pointing to source IP 65.240.22.1 network. Recommend
making the iframe visible. Fixing the code will correct the issue.
Correct Answer: B
QUESTION 8
An alert is issued from the SIEM that indicates a large number of failed logins for the same account name on one of the
application servers starting at 10:20 a.m. No other significant failed login activity is detected. Using Splunk to search for
activity pertaining to that account name, a security analyst finds the account has been authenticating successfully for
some time and started to fail this morning. The account is attempting to authenticate from an internal server that is
running a database to an application server. No other security activity is detected on the network. The analyst discovers
the account owner is a developer who no longer works for the company. Which of the following is the MOST likely
reason for the failed login attempts for that account?
A. The account that is failing to authenticate has not been maintained, and the company password change policy time frame has been reached for that account
B. The host-based firewall is blocking port 389 LDAP communication, preventing the login credentials from being
received by the application server
C. The license for the application has expired, and the failed logins will continue to occur until a new license key is
installed on the application
D. A successful malware attack has provided someone access to the network, and failed login attempts are an
indication of an attempt to privilege access to the application
Correct Answer: A
QUESTION 9
Organizational policies require vulnerability remediation on severity 7 or greater within one week. Anything with a severity less than 7 must be remediated within 30 days. The organization also requires security teams to investigate the
details of a vulnerability before performing any remediation. If the investigation determines the finding is a false positive,
no remediation is performed and the vulnerability scanner configuration is updated to omit the false positive from future scans:
The organization has three Apache web servers:
The results of a recent vulnerability scan are shown below: The team performs some investigation and finds a statement
from Apache:
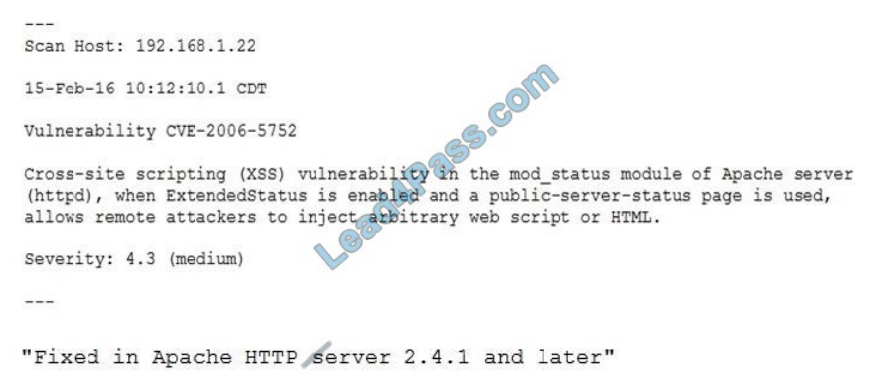
Which of the following actions should the security team perform?
A. Ignore the false positive on 192.168.1.22
B. Remediate 192.168.1.20 within 30 days
C. Remediate 192.168.1.22 within 30 days
D. Investigate the false negative on 192.168.1.20
Correct Answer: C
QUESTION 10
A company has several internal-only, web-based applications on the internal network. Remote employees are allowed
to connect to the internal corporate network with a company-supplied VPN client. During a project to upgrade the
internal application, contractors were hired to work on a database server and were given copies of the VPN client so
they could work remotely. A week later, a security analyst discovered an internal web-server had been compromised by
malware that originated from one of the contractor\\’s laptops. Which of the following changes should be made to BEST
counter the threat presented in this scenario?
A. Create a restricted network segment for contractors and set up a jump box for the contractors to use to access
internal resources.
B. Deploy a web application firewall in the DMZ to stop Internet-based attacks on the webserver.
C. Deploy an application layer firewall with network access control lists at the perimeter and then create alerts for
suspicious Layer 7 traffic.
D. Require the contractors to bring their laptops on-site when accessing the internal network instead of using the VPN
from a remote location.
E. Implement NAC to check for updated anti-malware signatures and location-based rules for PCs connecting to the
internal network.
Correct Answer: E
QUESTION 11
A logistics company\\’s vulnerability scan identifies the following vulnerabilities on Internet-facing devices in the DMZ:
SQL injection on an infrequently used web server that provides files to vendors SSL/TLS not used for a website that
contains promotional information
The scan also shows the following vulnerabilities on internal resources: Microsoft Office Remote Code Execution on test
server for a human resources system TLS downgrade vulnerability on a server in a development network
In order of risk, which of the following should be patched FIRST?
A. Microsoft Office Remote Code Execution
B. SQL injection
C. SSL/TLS not used
D. TLS downgrade
Correct Answer: A
QUESTION 12
A cybersecurity analyst is currently investigating a server outage. The analyst has discovered the following value was
entered for the username: 0xbfff601a. Which of the following attacks may be occurring?
A. Buffer overflow attack
B. Man-in-the-middle attack
C. Smurf attack
D. Format string attack
E. Denial of service attack
Correct Answer: D
QUESTION 13
A security analyst has discovered that an outbound SFTP process is occurring at the same time of day for the past
several days. At the time this was discovered, large amounts of business-critical data were delivered. The authentication
for this process occurred using a service account with proper credentials. The security analyst investigated the
destination IP for this transfer and discovered that this new process is not documented in the change management log.
Which of the following would be the BEST course of action for the analyst to take?
A. Investigate a potential incident.
B. Verify user permissions.
C. Run a vulnerability scan.
D. Verify SLA with the cloud provider.
Correct Answer: A
latest updated CompTIA cs0-001 exam questions from the leads4pass cs0-001 dumps! 100% pass the cs0-001 exam! Download leads4pass cs0-001 VCE and PDF dumps: https://www.leads4pass.com/cs0-001.html (Q&As: 416 dumps)
Get free CompTIA cs0-001 dumps PDF online: https://drive.google.com/file/d/1MaCotAg3BQj1g1fidH-fZjbpFsyQftqh/

