The latest CompTIA cs0-002 dumps by leads4pass helps you pass the cs0-002 exam for the first time! leads4pass Latest Update CompTIA cs0-002 VCE Dump and cs0-002 PDF Dumps, leads4pass cs0-002 Exam Questions Updated, Answers corrected! Get the latest LeadPass cs0-002 dumps with Vce and PDF: https://www.leads4pass.com/cs0-002.html (Q&As: 119 dumps)
[Free cs0-002 PDF] CompTIA cs0-002 Dumps PDF can be collected on Google Drive shared by leads4pass:
https://drive.google.com/file/d/1UEiAFAb7pRh89miPtx-BpUNFkjfxeTu3/
[leads4pass cs0-002 Youtube] CompTIA cs0-002 Dumps can be viewed on Youtube shared by leads4pass
CompTIA cs0-002 Online Exam Practice Questions
QUESTION 1
Bootloader malware was recently discovered on several company workstations. All the workstations run Windows and
are current models with UEFI capability. Which of the following UEFI settings is the MOST likely cause of the
infections?
A. Compatibility mode
B. Secure boot mode
C. Native mode
D. Fast boot mode
Correct Answer: A
QUESTION 2
A security analyst for a large financial institution is creating a threat model for a specific threat actor that is likely
targeting an organization\\’s financial assets. Which of the following is the BEST example of the level of sophistication
this threat actor is using?
A. Social media accounts attributed to the threat actor
B. Custom malware attributed to the threat actor from prior attacks
C. Email addresses and phone numbers tied to the threat actor
D. Network assets used in previous attacks attributed to the threat actor
E. IP addresses used by the threat actor for command and control
Correct Answer: D
QUESTION 3
The security team at a large corporation is helping the payment-processing team to prepare for a regulatory compliance
audit and meet the following objectives:
Reduce the number of potential findings by the auditors.
Limit the scope of the audit to only devices used by the payment-processing team for activities directly impacted by the
regulations.
Prevent the external-facing web infrastructure used by other teams from coming into the scope.
Limit the amount of exposure the company will face if the systems used by the payment-processing team are
compromised.
Which of the following would be the MOST effective way for the security team to meet these objectives?
A. Limit the permissions to prevent other employees from accessing data owned by the business unit.
B. Segment the servers and systems used by the business unit from the rest of the network.
C. Deploy patches to all servers and workstations across the entire organization.
D. Implement full-disk encryption on the laptops used by employees of the payment-processing team.
Correct Answer: B
QUESTION 4
While planning segmentation for an ICS environment, a security engineer determines IT resources will need access to
devices within the ICS environment without compromising security. To provide the MOST secure access model in this
scenario, the jump box should be __________.
A. placed in an isolated network segment, authenticated on the IT side, and forwarded into the ICS network.
B. placed on the ICS network with a static firewall rule that allows IT network resources to authenticate.
C. bridged between the IT and operational technology networks to allow authenticated access.
D. placed on the IT side of the network, authenticated, and tunneled into the ICS environment.
Correct Answer: A
QUESTION 5
A SIEM solution alerts a security analyst of a high number of login attempts against the company\\’s webmail portal. The
analyst determines the login attempts used credentials from a past data breach. Which of the following is the BEST
mitigation to prevent unauthorized access?
A. Single sign-on
B. Mandatory access control
C. Multifactor authentication
D. Federation
E. Privileged access management
Correct Answer: C
QUESTION 6
A security analyst is building a malware analysis lab. The analyst wants to ensure malicious applications are not
capable of escaping the virtual machines and pivoting to other networks. To BEST mitigate this risk, the analyst should
use __________.
A. an 802.11ac wireless bridge to create an air gap.
B. a managed switch to segment the lab into a separate VLAN.
C. a firewall to isolate the lab network from all other networks.
D. an unmanaged switch to segment the environments from one another.
Correct Answer: B
QUESTION 7
A security analyst has received information from a third-party intelligence-sharing resource that indicates employee
accounts were breached. Which of the following is the NEXT step the analyst should take to address the issue?
A. Audit access permissions for all employees to ensure the least privilege.
B. Force a password reset for the impacted employees and revoke any tokens.
C. Configure SSO to prevent passwords from going outside the local network.
D. Set up privileged access management to ensure auditing is enabled.
Correct Answer: B
QUESTION 8
During routine monitoring, a security analyst discovers several suspicious websites that are communicating with the localhost. The analyst queries for IP 192.168.50.2 for a 24-hour period: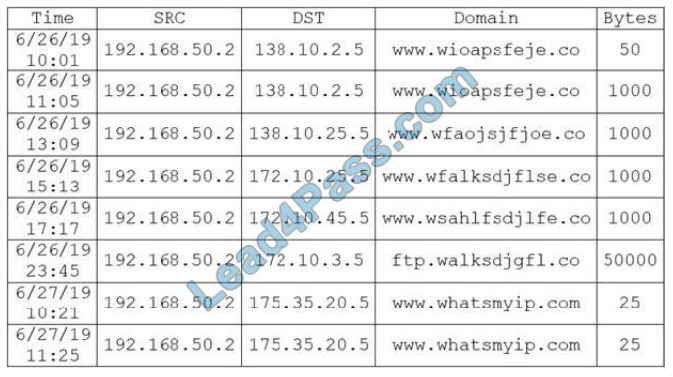
To further investigate, the analyst should request PCAP for SRC 192.168.50.2 and __________.
A. DST 138.10.2.5.
B. DST 138.10.25.5.
C. DST 172.10.3.5.
D. DST 172.10.45.5.
E. DST 175.35.20.5.
Correct Answer: C
QUESTION 9
A security analyst is trying to determine if a host is active on a network. The analyst first attempts the following: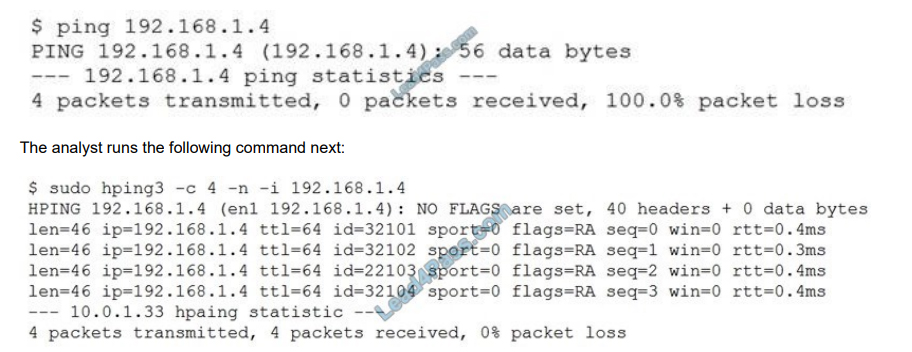
Which of the following would explain the difference in results?
A. ICMP is being blocked by a firewall.
B. The routing tables for ping and hping3 were different.
C. The original ping command needed root permission to execute.
D. hping3 is returning a false positive.
Correct Answer: A
QUESTION 10
A security analyst has received reports of very slow, intermittent access to a public-facing corporate server. Suspecting
the system may be compromised, the analyst runs the following commands:
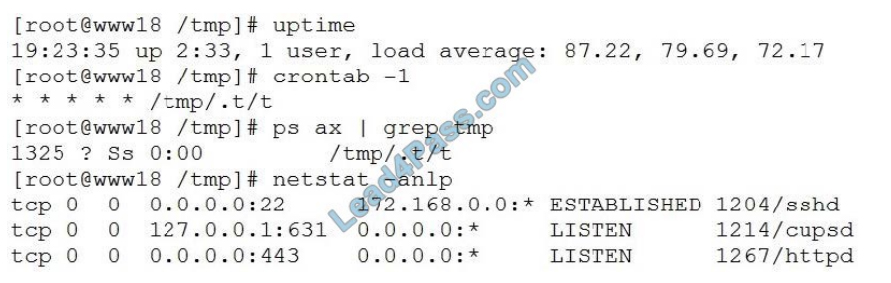
Based on the output from the above commands, which of the following should the analyst do NEXT to further the
investigation?
A. Run crontab -r; rm -rf /tmp/.t to remove and disable the malware on the system.
B. Examine the server logs for further indicators of compromise of a web application.
C. Run kill -9 1325 to bring the load average down so the server is usable again.
D. Perform a binary analysis on the /tmp/.t/t file, as it is likely to be a rogue SSHD server.
Correct Answer: B
QUESTION 11
A development team uses open-source software and follows an Agile methodology with two-week sprints. Last month,
the security team filed a bug for an insecure version of a common library. The DevOps team updated the library on the
server, and then the security team rescanned the server to verify it was no longer vulnerable. This month, the security
team found the same vulnerability on the server.
Which of the following should be done to correct the cause of the vulnerability?
A. Deploy a WAF in front of the application.
B. Implement a software repository management tool.
C. Install a HIPS on the server.
D. Instruct the developers to use input validation in the code.
Correct Answer: B
QUESTION 12
Which of the following software security best practices would prevent an attacker from being able to run arbitrary SQL
commands within a web application? (Choose two.)
A. Parameterized queries
B. Session management
C. Input validation
D. Output encoding
E. Data protection
F. Authentication
Correct Answer: AC
Reference: https://www.ptsecurity.com/ww-en/analytics/knowledge-base/how-to-prevent-sql-injection-attacks/
QUESTION 13
A security analyst reviews the following aggregated output from a Nmap scan and the border firewall ACL: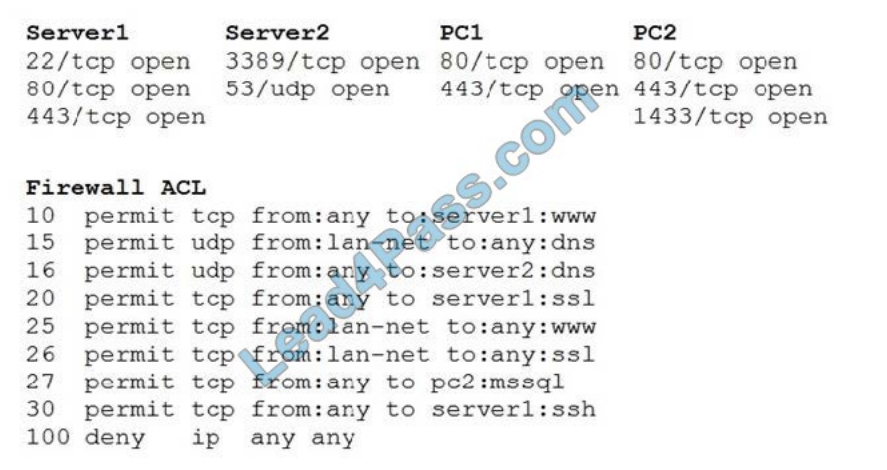
Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current
functionality?
A. PC1
B. PC2
C. Server1
D. Server2
E. Firewall
Correct Answer: E
latest updated CompTIA cs0-002 exam questions from the leads4pass cs0-002 dumps! 100% pass the cs0-002 exam! Download leads4pass cs0-002 VCE and PDF dumps: https://www.leads4pass.com/cs0-002.html (Q&As: 119 dumps)
Get free CompTIA cs0-002 dumps PDF online: https://drive.google.com/file/d/1UEiAFAb7pRh89miPtx-BpUNFkjfxeTu3/

