The latest Microsoft AZ-303 dumps by leads4pass helps you pass the AZ-303 exam for the first time! leads4pass Latest Update Microsoft AZ-303 VCE Dump and AZ-303 PDF Dumps, leads4pass AZ-303 Exam Questions Updated, Answers corrected! Get the latest LeadPass AZ-303 dumps with Vce and PDF: https://www.leads4pass.com/az-303.html (Q&As: 111 dumps)
[Free AZ-303 PDF] Microsoft AZ-303 Dumps PDF can be collected on Google Drive shared by leads4pass:
https://drive.google.com/file/d/1wkx74ntbkdk4ul65PBkC9gSoigufb7Zm/
[leads4pass AZ-303 Youtube] Microsoft AZ-303 Dumps can be viewed on Youtube shared by leads4pass
Microsoft AZ-303 Online Exam Practice Questions
QUESTION 1
You have a server named Server1 that runs Windows Server 2019. Server1 is a container host.
You are creating a Dockerfile to build a container image.
You need to add a file named File1.txt from Server1 to a folder named C:\Folder1 in the container image.
Solution: You add the following line to the Dockerfile.
COPY File1.txt /Folder1/
You then build the container image.
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
The copy is the correct command to copy a file to the container image.
Reference: https://docs.docker.com/develop/develop-images/dockerfile_best-practices/#add-or-copy
https://docs.docker.com/engine/reference/builder/
QUESTION 2
HOTSPOT
You plan to deploy an Azure virtual machine named VM1 by using an Azure Resource Manager template.
You need to complete the template.
What should you include in the template? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
Within your template, the dependsOn element enables you to define one resource as dependent on one or more
resources. Its value can be a comma-separated list of resource names.
Box 1: \\’Microsoft.Network/networkInterfaces\\’
This resource is a virtual machine. It depends on two other resources:
Microsoft.Storage/storage accounts
Microsoft.Network/networkInterfaces
Box 2: \\’Microsoft.Network/virtual networks/\\’
The dependsOn element enables you to define one resource as dependent on one or more resources. The resource
depends on two other resources:
Microsoft.Network/public IP addresses
Microsoft.Network/virtual networks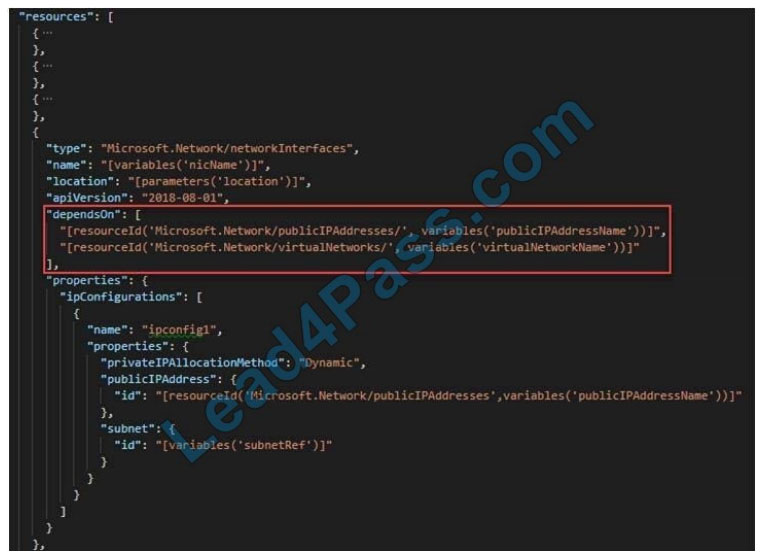
QUESTION 3
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
A user named Admin1 attempts to create an access review from the Azure Active Directory admin center and discovers
that the Access review settings are unavailable. Admin1 discovers that all the other identity Governance settings are
available.
Admin1 is assigned the User administrator, Compliance administrator, and Security administrator roles.
You need to ensure that Admin1 can create access reviews in contoso.com.
Solution: You purchase an Azure Directory Premium P2 license for contoso.com.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
Instead, use Azure AD Privileged Identity Management.
Note: PIM essentially helps you manage the who, what, when, where, and why for resources that you care about. Key
features of PIM include: Conduct access reviews to ensure users still need roles
Reference: https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
QUESTION 4
You have resources in three Azure regions. Each region contains two virtual machines. Each virtual machine has a
the public IP address assigned to its network interface and a locally installed application named App1.
You plan to implement Azure Front Door-based load balancing across all the virtual machines.
You need to ensure that App1 on the virtual machines will only accept traffic routed from Azure Front Door.
What should you implement?
A. Azure Private Link
B. service endpoints
C. network security groups (NSGs) with service tags
D. network security groups (NSGs) with application security groups
Correct Answer: C
Configure IP ACLing for your backends to accept traffic from Azure Front Door\\’s backend IP address space and
Azure\\’s infrastructure services only. Refer to the IP details below for ACLing your backend:
Refer AzureFrontDoor.Backend section in Azure IP Ranges and Service Tags for Front Door\\’s IPv4 backend IP
address range or you can also use the service tag AzureFrontDoor.Backend in your network security groups.
Reference:
https://docs.microsoft.com/en-us/azure/frontdoor/front-door-faq
QUESTION 5
You have an Azure subscription that contains 100 virtual machines.
You have a set of Pester tests in PowerShell that validate the virtual machine environment.
You need to run the tests whenever there is an operating system update on the virtual machines. The solution must
minimize implementation time and recurring costs.
Which three resources should you use to implement the tests? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Azure Automation runbook
B. an alert rule
C. an Azure Monitor query
D. a virtual machine that has network access to the 100 virtual machines
E. an alert action group
Correct Answer: ABE
AE: You can call Azure Automation runbooks by using action groups or by using classic alerts to automate tasks based
on alerts.
B: Alerts are one of the key features of Azure Monitor. They allow us to alert on actions within an Azure subscription
Reference: https://docs.microsoft.com/en-us/azure/automation/automation-create-alert-triggered-runbook
https://techsnips.io/snips/how-to-create-and-test-azure-monitor-alerts/?page=13
QUESTION 6
HOTSPOT
You plan to create an Azure Storage account in the Azure region of East US 2.
You need to create a storage account that meets the following requirements:
Replicates synchronously
Remains available if a single data center in the region fails
How should you configure the storage account? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: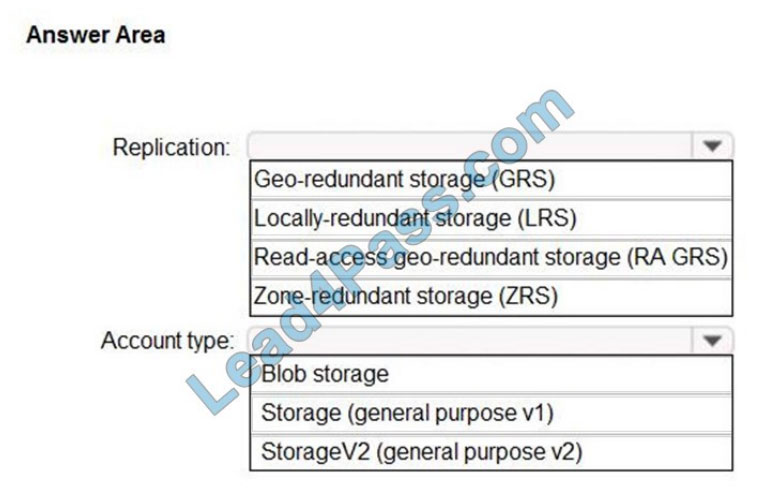
Correct Answer:
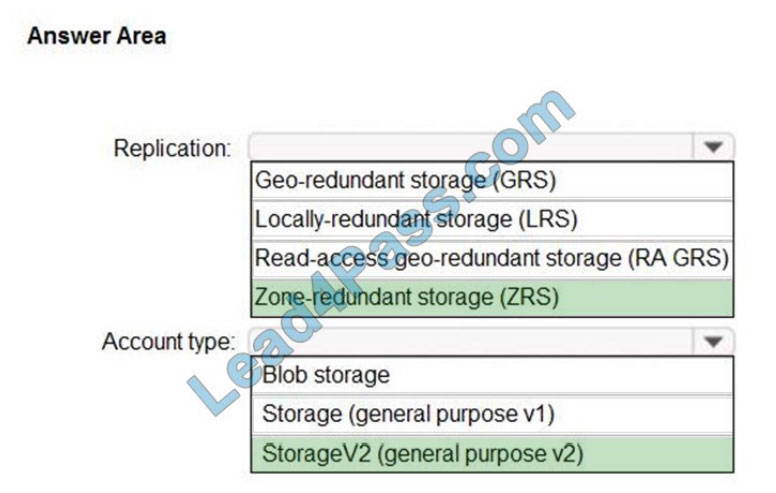
Box 1: Zone-redundant storage (ZRS)
Zone-redundant storage (ZRS) replicates your data synchronously across three storage clusters in a single region.
LRS would not remain available if a data center in the region fails
GRS and RA GRS use asynchronous replication.
Box 2: StorageV2 (general purpose V2)
ZRS only supports GPv2.
Reference:
https://docs.microsoft.com/en-us/azure/storage/common/storage-redundancy
https://docs.microsoft.com/en-us/azure/storage/common/storage-redundancy-zrs
QUESTION 7
Your company has an Azure subscription.
You enable multi-factor authentication (MFA) for all users.
The company\\’s help desk reports an increase in calls from users who receive MFA requests while they work from the
company\\’s main office.
You need to prevent the users from receiving MFA requests when they sign in from the main office.
What should you do?
A. From Conditional access in Azure Active Directory (Azure AD), create a named location.
B. From the MFA service settings create a trusted IP range.
C. From Conditional access in Azure Active Directory (Azure AD), create a custom control.
D. From Azure Active Directory (Azure AD), configure organizational relationships.
Correct Answer: B
The first thing you may want to do, before enabling Multi-Factor Authentication for any users, is to consider configuring
some of the available settings. One of the most important features is a trusted IPs list. This will allow you to whitelist a
range of IPs for your network. This way, when users are in the office, they will not get prompted with MFA, and when
they take their devices elsewhere, they will. Here\\’s how to do it:
Log in to your Azure Portal.
Navigate to Azure AD > Conditional Access > Named locations.
From the top toolbar select, Configure MFA trusted IPs.
Reference:
https://www.kraftkennedy.com/implementing-azure-multi-factor-authentication/
QUESTION 8
HOTSPOT
You need to identify the storage requirements for Contoso.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: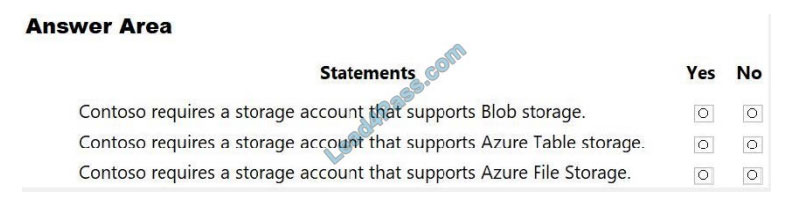
Correct Answer:

Box 1: Yes
Scenario: Move the existing product blueprint files to Azure Blob storage.
Scenario: Use unmanaged standard storage for the hard disks of the virtual machines.
Page blobs are optimized for writes at random locations within a blob. They also support Unmanaged Disks.
Scenario:
SQL Server Data Files in Microsoft Azure enables native support for SQL Server database files stored as blobs. It
allows you to create a database in SQL Server running in on-premises or in a virtual machine in Microsoft Azure with a
dedicated storage location for your data in Microsoft Azure Blob storage.
Box 2: No
Box 3: No
Reference:
https://docs.microsoft.com/en-us/sql/relational-databases/databases/sql-server-data-files-in-microsoft-azure
QUESTION 9
You have an Azure App Service app.
You need to implement tracing for the app. The tracing information must include the following:
Usage trends AJAX call responses Page load speed by browser Server and browser exceptions
What should you do?
A. Configure IIS logging in Azure Log Analytics.
B. Configure a connection monitor in Azure Network Watcher.
C. Configure custom logs in Azure Log Analytics.
D. Enable the Azure Application Insights site extension.
Correct Answer: D
For web pages, Application Insights JavaScript SDK automatically collects AJAX calls as dependencies.
Note: Some of the things you can track or collect are:
What are the most popular webpages in your application, at what time of day and where is that traffic coming from?
Dependency rates or response times and failure rates to find out if their \\’s an external service that\\’s causing
performance issues on your app, maybe a user is using a portal to get through to your application and there are
response time
issues going through there for instance.
Exceptions for both server and browser information, as well as page views and load performance from the end users\\’
side.
Reference:
https://azure.microsoft.com/en-us/blog/ajax-collection-in-application-insights/
https://blog.pragmaticworks.com/what-is-application-insights
QUESTION 10
HOTSPOT
Your company has an Azure Container Registry named Registry1.
You have an Azure virtual machine named Server1 that runs Windows Server 2019.
From Server1, you create a container image named image1.
You need to add image1 to Registry1.
Which command should you run on Server1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
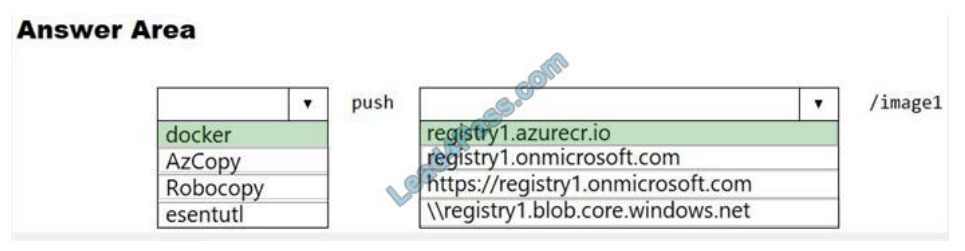
An Azure container registry stores and manages private Docker container images, similar to the way Docker Hub stores
public Docker images. You can use the Docker command-line interface (Docker CLI) for login, push, pull, and other
operations on your container registry.
Reference: https://docs.microsoft.com/en-us/azure/container-registry/container-registry-get-started-docker-cli
https://docs.docker.com/engine/reference/commandline/push/
QUESTION 11
HOTSPOT
You have an Azure subscription.
You plan to deploy an app that has a web front end and an application tier.
You need to recommend a load balancing solution that meets the following requirements:
Internet to web tier:
-Provides URL-based routing
-Supports connection draining
-Prevents SQL injection attacks
Web tier to application tier:
-Provides port forwarding
–
Supports HTTPS health probes
–
Supports an availability set as a backend pool
Which load balancing solution should you recommend for each tier? To answer, select the appropriate options in the
answer area.
NOTE: Each correct selection is worth one point.
Hot Area: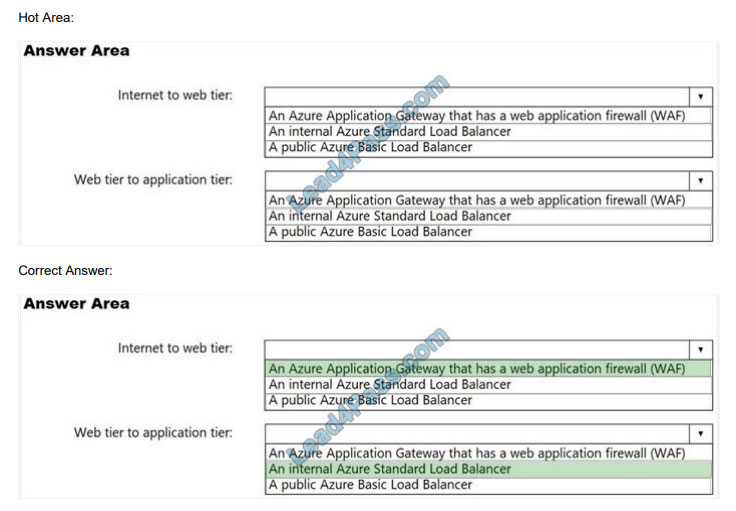
Box 1: An Azure Application Gateway that has a web application firewall (WAF)
Azure Application Gateway offers a web application firewall (WAF) that provides centralized protection of your web
applications from common exploits and vulnerabilities. Web applications are increasingly targeted by malicious attacks
that
exploit commonly known vulnerabilities. SQL injection and cross-site scripting are among the most common attacks.
Application Gateway operates as an application delivery controller (ADC). It offers Secure Sockets Layer (SSL)
termination, cookie-based session affinity, round-robin load distribution, content-based routing, ability to host multiple
websites,
and security enhancements.
Box 2: An internal Azure Standard Load Balancer
The internet to web tier is the public interface, while the web tier to application tier should be internal.
Note: When using load-balancing rules with Azure Load Balancer, you need to specify a health probe to allow Load
Balancer to detect the backend endpoint status.
Health probes support the TCP, HTTP, HTTPS protocols.
Reference:
https://docs.microsoft.com/en-us/azure/application-gateway/waf-overview
https://docs.microsoft.com/en-us/azure/load-balancer/load-balancer-custom-probe-overview
QUESTION 12
You have a virtual network named VNet1 as shown in the exhibit. (Click the Exhibit tab.)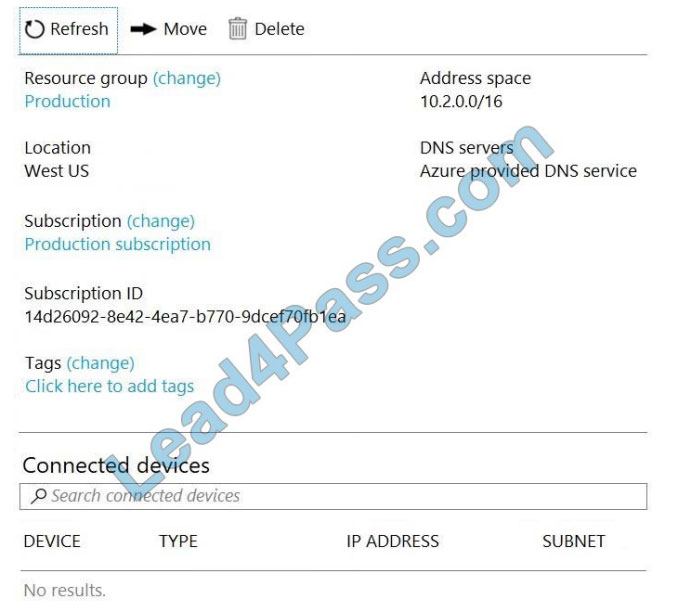
No devices are connected to VNet1.
You plan to peer VNet1 to another virtual network named VNet2. VNet2 has an address space of 10.2.0.0/16.
You need to create the peering.
What should you do first?
A. Configure a service endpoint on VNet2.
B. Add a gateway subnet to VNet1.
C. Create a subnet on VNEt1 and VNet2.
D. Modify the address space of VNet1.
Correct Answer: D
The virtual networks you peer must have non-overlapping IP address spaces. The exhibit indicates that VNet1 has an
address space of 10.2.0.0/16, which is the same as VNet2, and thus overlaps. We need to change the address space
for VNet1.
Reference: https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-manage-peering#requirements-andconstraints
QUESTION 13
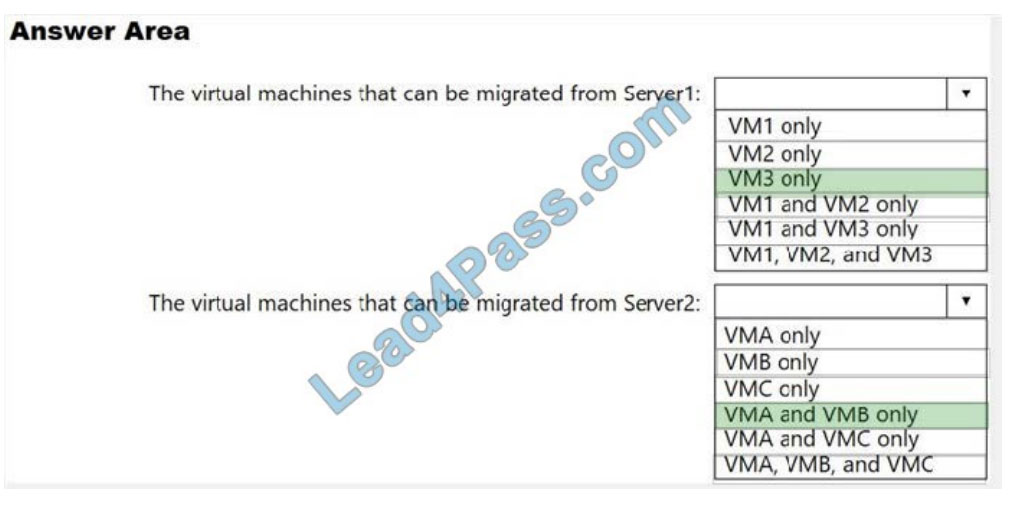
HOTSPOT
Your company has a virtualization environment that contains the virtualization hosts shown in the following table.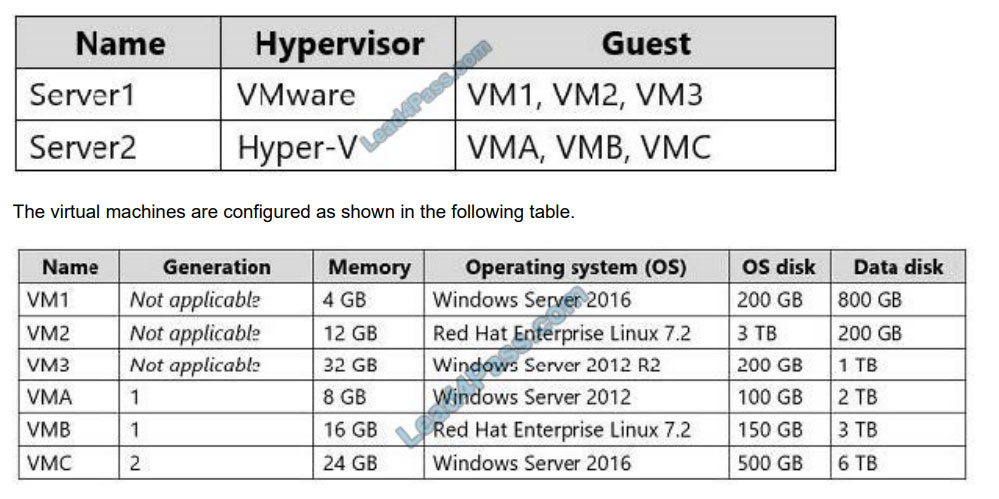
All virtual machines use basic disks. VM1 is protected by using BitLocker Drive Encryption (BitLocker).
You plan to migrate the virtual machines to Azure by using Azure Site Recovery.
You need to identify which virtual machines can be migrated.
Which virtual machines should you identify for each server? To answer, select the appropriate options in the answer
area.
NOTE: Each correct selection is worth one point.
Hot Area: 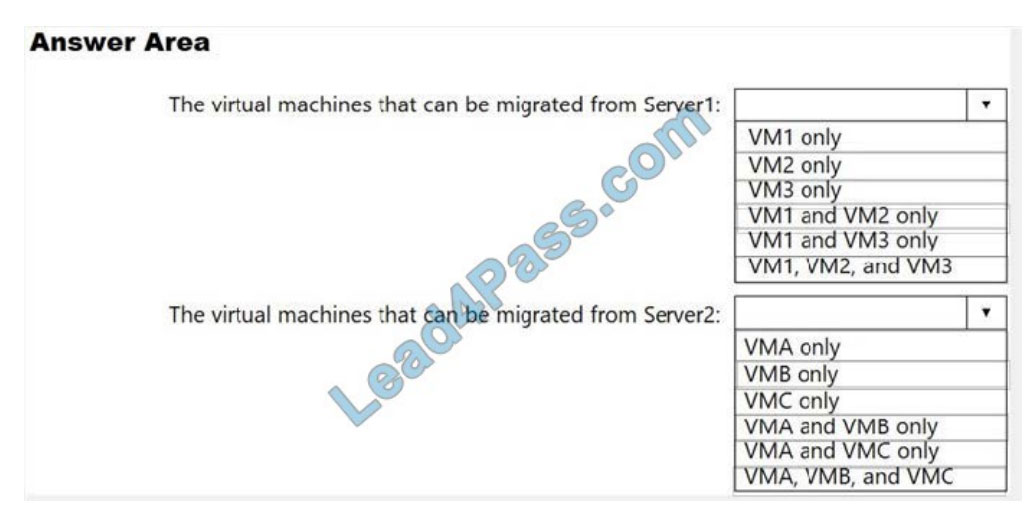
Correct Answer:
latest updated Microsoft AZ-303 exam questions from the leads4pass AZ-303 dumps! 100% pass the AZ-303 exam! Download leads4pass AZ-303 VCE and PDF dumps: https://www.leads4pass.com/az-303.html (Q&As: 111 dumps)
Get free Microsoft AZ-303 dumps PDF online: https://drive.google.com/file/d/1wkx74ntbkdk4ul65PBkC9gSoigufb7Zm/

