
The Microsoft SC-300 exam certification is very popular, and passing the SC-300 exam is something to be proud of! This site shares how to pass the SC-300 exam!
We also shared the Microsoft SC-300 exam questions in the early days, and the response was very good! This time I’m sharing the latest free topic updated in November. Our purpose is to help you progress!
Of course, I don’t have to go around the big circle. The free Microsoft SC-300 practice questions can make you progress, but they cannot help you pass the exam 100%.
Our ultimate goal is to recommend you leads4pass SC-300 dumps https://www.leads4pass.com/sc-300.html. leads4pass SC-300 dumps have a complete test question, all questions are updated in real-time, to ensure that it is true and effective!
Next, let’s practice online first!
Microsoft SC-300 online practice questions
The answer to the question is at the end of the article
QUESTION 1
You have a Microsoft 365 tenant.
All users have mobile phones and laptops.
The users frequently work from remote locations that do not have Wi-Fi access or mobile phone connectivity.
While working from the remote locations, the users connect their laptop to a wired network that has internet access.
You plan to implement multi-factor authentication (MFA).
Which MFA authentication method can the users use from the remote location?
A. a notification through the Microsoft Authenticator app
B. an app password
C. Windows Hello for Business
D. SMS
In Windows 10, Windows Hello for Business replaces passwords with strong two-factor authentication on PCs and mobile devices.
This authentication consists of a new type of user credential that is tied to a device and uses a biometric or PIN.
After an initial two-step verification of the user during enrollment, Windows Hello is set up on the user\\’s device and Windows asks the user to set a gesture, which can be a biometric, such as a fingerprint, or a PIN.
The user provides the gesture to verify their identity. Windows then uses Windows Hello to authenticate users.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-authentication-methods
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-overview
QUESTION 2
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
You plan to bulk invite Azure AD business-to-business (B2B) collaboration users.
Which two parameters must you include when you create the bulk invite?
Each correct answer presents part of the solution NOTE: Each correct selection is worth one point.
A. email address
B. redirection URL
C. username
D. shared key
E. password
Reference: https://docs.microsoft.com/en-us/azure/active-directory/external-identities/tutorial-bulk-invite
QUESTION 3
HOTSPOT
You need to meet the technical requirements for the probability that user identities were compromised.
What should the users do first, and what should you configure?
To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
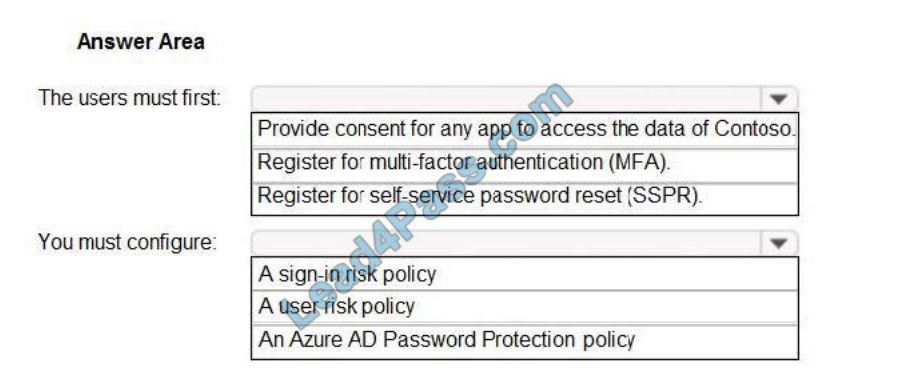
Correct Answer:
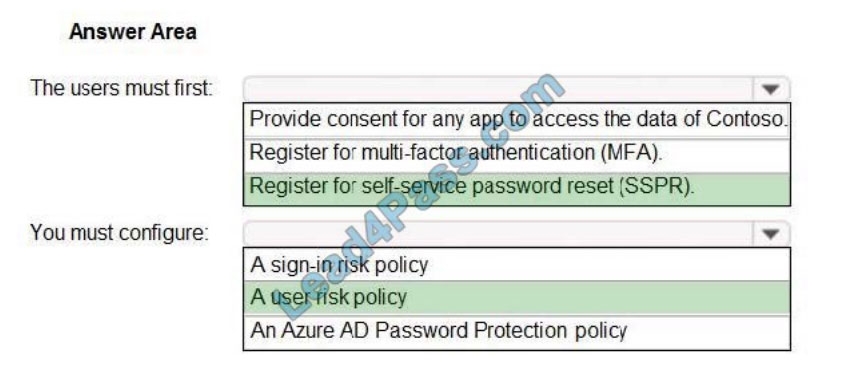
QUESTION 4
Note: This question is part of a series of questions that present the same scenario.
Each question in the series contains a unique solution that might meet the stated goals.
Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it.
As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant that syncs to an Active Directory forest.
You discover that when a user account is disabled in Active Directory, the disabled user can still authenticate to Azure AD for up to 30 minutes.
You need to ensure that when a user account is disabled in Active Directory, the user account is immediately prevented from authenticating to Azure AD.
Solution: You configure password writeback.
Does this meet the goal?
A. Yes
B. No
Reference: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/choose-ad-authn
QUESTION 5
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant that contains an administrative unit named Department1.
Department1 has the users shown in the Users exhibit. (Click the Users tab.)
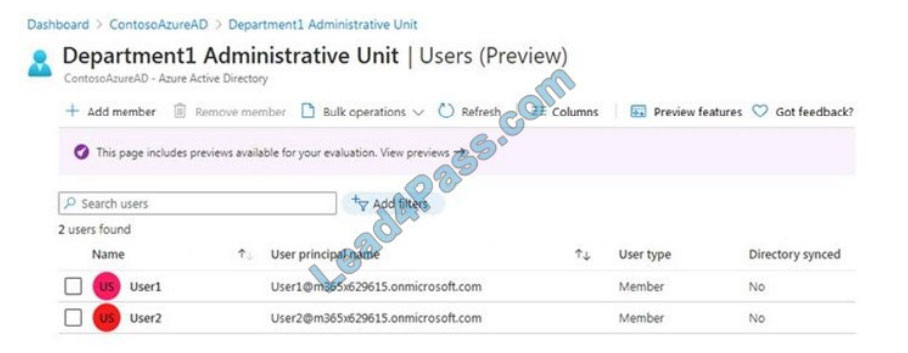
Department1 has the groups shown in the Groups exhibit. (Click the Groups tab.) Department1 has the user
administrator assignments shown in the Assignments exhibit. (Click the Assignments tab.)
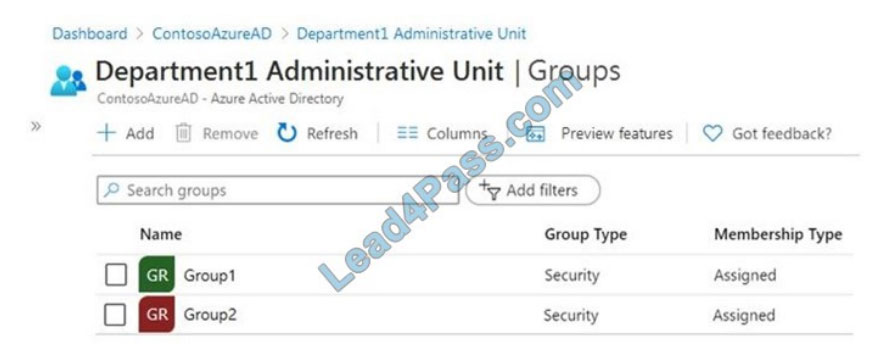
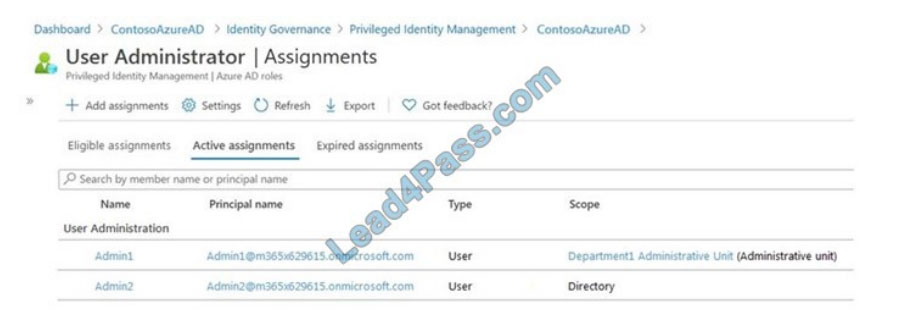
The members of Group2 are shown in the Group2 exhibit. (Click the Group2 tab.)
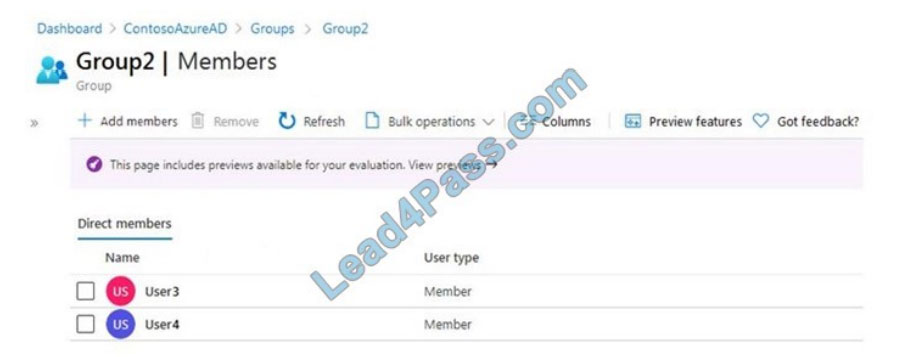
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
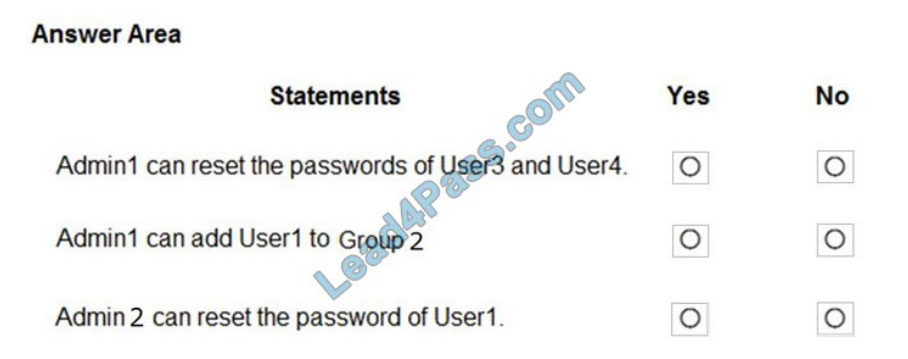
Correct Answer:
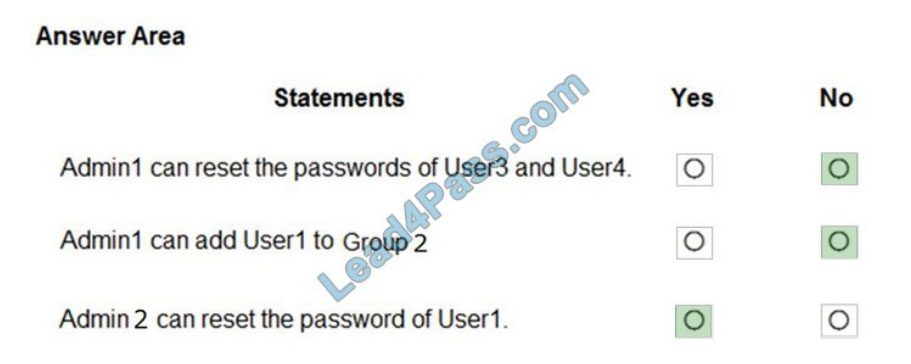
QUESTION 6
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains an Azure AD enterprise application named App1.
A contractor uses the credentials of [email protected].
You need to ensure that you can provide the contractor with access to App1.
The contractor must be able to authenticate as [email protected].
What should you do?
A. Run the New-AzADUser cmdlet.
B. Configure the External collaboration settings.
C. Add a WS-Fed identity provider.
D. Create a guest user account in contoso.com.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/external-identities/b2b-quickstart-add-guestusersportal
QUESTION 7
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant that contains three users named User1, User1, and User3, You create a group named Group1.
You add User2 and User3 to Group1.
You configure a role in Azure AD Privileged identity Management (PIM) as shown in the application administrator exhibit. (Click the application Administrator tab.)
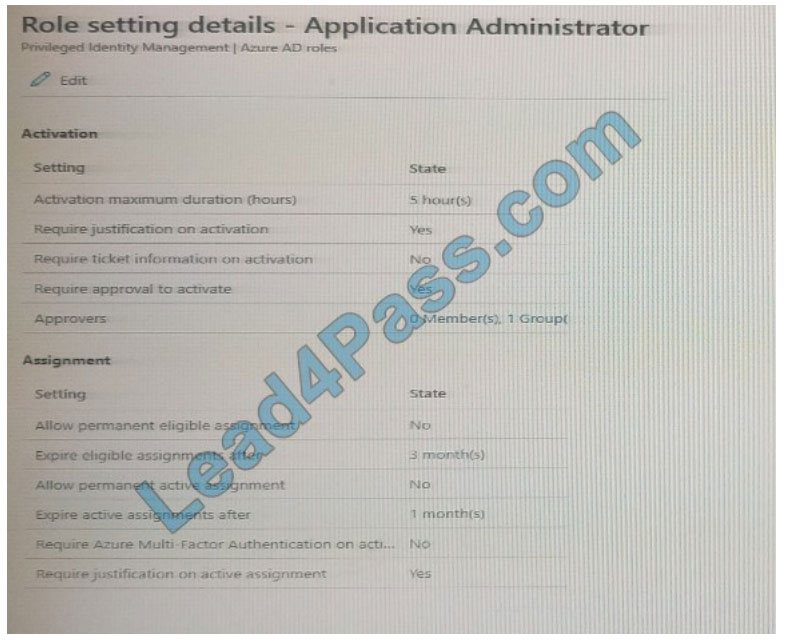
Group1 is configured as the approver for the application administrator role.
You configure User2to be eligible for the application administrator role.
For User1, you add an assignment to the Application administrator role as shown in the Assignment exhibit. (Click Assignment tab)
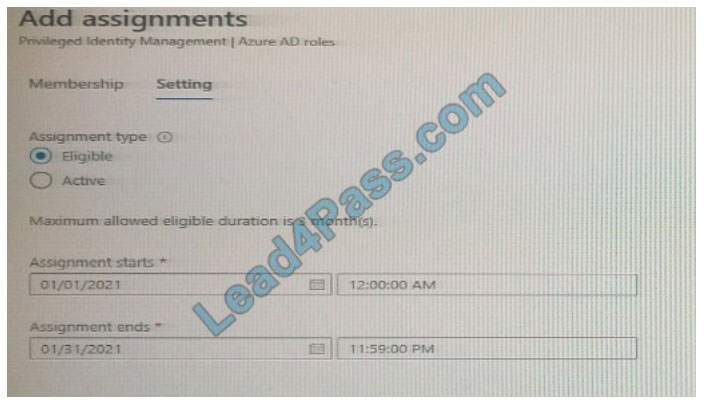
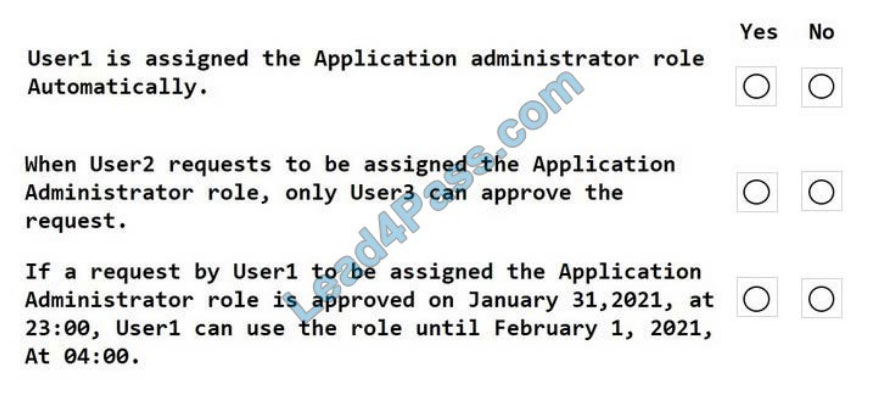
For each of the following statement, select Yes if the statement is true, Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
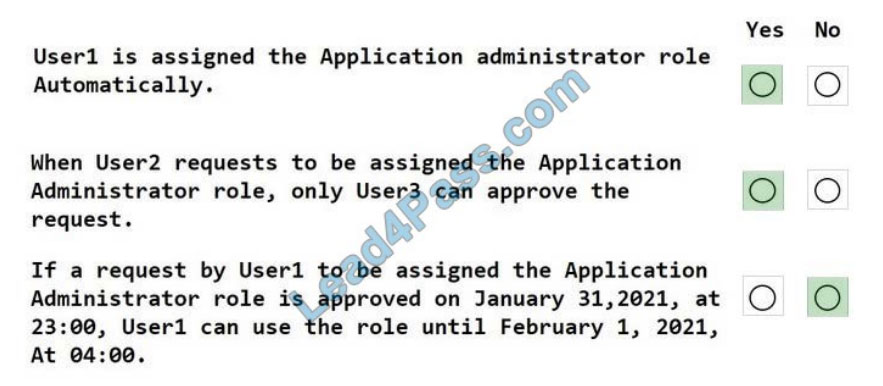
Correct Answer:
QUESTION 8
You need to locate licenses to the A. Datum users. The solution must need the technical requirements.
Which type of object should you create?
A. A Dynamo User security group
B. An OU
C. A distribution group
D. An administrative unit
QUESTION 9
You need to configure the detection of multi-staged attacks to meet the monitoring requirements.
What should you do?
A. Customize the Azure Sentinel rule logic.
B. Create a workbook.
C. Add Azure Sentinel data connectors.
D. Add an Azure Sentinel playbook.
QUESTION 10
You have an Azure Active Directory (Azure AD) tenant that contains the groups shown in the following table.
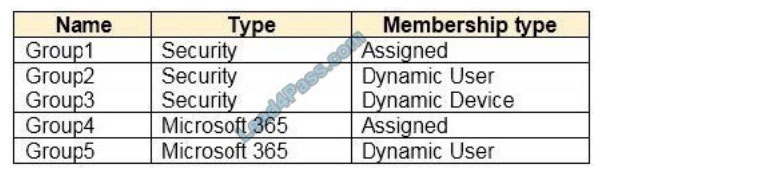
For which groups can you create an access review?
A. Group1 only
B. Group1 and Group4 only
C. Group1 and Group2 only
D. Group1, Group2, Group4, and Group5 only
E. Group1, Group2, Group3, Group4 and Group5
You cannot create access reviews for device groups.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/governance/create-access-review
QUESTION 11
Your company recently implemented Azure Active Directory (Azure AD) Privileged Identity Management (PIM).
While you review the roles in PIM, you discover that all 15 users in the IT department at the company have permanent security administrator rights.
You need to ensure that the IT department users only have access to the Security administrator role when required.
What should you configure for the Security administrator role assignment?
A. Expire eligible assignments after from the Role settings details
B. Expire active assignments after from the Role settings details
C. Assignment type to Active
D. Assignment type to Eligible
Reference: https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
QUESTION 12
You have a Microsoft 365 tenant.
In Azure Active Directory (Azure AD), you configure the terms of use.
You need to ensure that only users who accept the terms of use can access the resources in the tenant. Other users must be denied access.
What should you configure?
A. an access policy in Microsoft Cloud App Security.
B. Terms and conditions in Microsoft Endpoint Manager.
C. a conditional access policy in Azure AD
D. a compliance policy in Microsoft Endpoint Manager
Reference: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/terms-of-use
QUESTION 13
You configure a new Microsoft 36S tenant to use a default domain name of contosso.com.
You need to ensure that you can control access to Microsoft 365 resource-, by using conditional access policy.
What should you do first?
A. Disable the User consent settings.
B. Disable Security defaults.
C. Configure a multi-factor authentication (Ml A) registration policy1.
D. Configure password protection for Windows Server Active Directory.
Validation results:
| Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 |
| C | AB | image | B | image | D | image | A | A | D | D | C | B |
If you like PDF mode!
Microsoft SC-300 exam PDF download online
Google Drive: https://drive.google.com/file/d/170TcAnfni9MQeYbAXoqUKvZxRfNqnA2f/view?usp=sharing
The above Microsoft SC-300 practice questions can verify your ability! To pass the exam 100%,
please select the complete Microsoft SC-300 dumps https://www.leads4pass.com/sc-300.html (total questions: 117 Q&A). Help you successfully pass the first exam.
We will continue to update all Microsoft exam questions! Follow us for more!

